
Passing the Microsoft SC-200 exam will protect your job and increase your income under the premise of society’s rapid and intelligent development in 2024. Therefore, this blog brings you a new exam SC-200 study guide and new SC-200 exam questions to help you study for the Microsoft Security Operations Analyst exam.
Security Operations Analyst Associate Technical Certifications
Exam SC-200: Security Operations Analyst Associate is a technical certification. Liam Tung, a writer on the Zdnet.com website, spoke highly of the certification as the art and tool of self-defense. Primarily to teach you to investigate, search, and mitigate threats using Microsoft Sentinel, Microsoft Defender for Cloud, and Microsoft 365 Defender.
Now that we’re done with certification, let’s return to the exam.
SC-200 Exam Details Section
Prerequisites: Basic understanding of Microsoft security, compliance, and identity products, a basic understanding of Microsoft 365, familiarity with Microsoft Azure services, virtual machines, and virtual networks, and familiarity with Windows and Linux operating systems
The following resources are beneficial for the exam:
https://learn.microsoft.com/en-us/azure/security/fundamentals/overview
https://learn.microsoft.com/en-us/microsoft-365/security/?view=o365-worldwide
https://learn.microsoft.com/en-us/azure/security/fundamentals/identity-management-overview
https://learn.microsoft.com/en-us/training/paths/describe-concepts-of-security-compliance-identity/
https://learn.microsoft.com/en-us/training/paths/describe-capabilities-of-microsoft-identity-access/
https://learn.microsoft.com/en-us/training/paths/describe-capabilities-of-microsoft-security-solutions/
https://learn.microsoft.com/en-us/training/paths/describe-capabilities-of-microsoft-compliance-solutions/
https://learn.microsoft.com/en-us/training/modules/azure-well-architected-security/
Exam topics and weighting: Manage a security operations environment (25–30%), Configure protections and detections (15–20%), Manage incident response (35–40%), Perform threat hunting (15–20%)
Exam duration: 100 minutes
Number of questions: between 40-60
Exam format: Invigilated by an invigilator and not open-book. There may be interactive sections.
What areas does the SC-200 exam focus on: Microsoft Azure, Microsoft 365
Exam languages: English, Japanese, Chinese (Simplified), Korean, French, German, Spanish, Portuguese (Brazilian), Chinese (Traditional), Italian
How to schedule an exam: Pearson Vue
Cost of taking the exam: $165
Passing score: 700 points
Master the skills: Mitigate threats with Microsoft 365 Defender, mitigate threats with Defender for Cloud, and mitigate threats with Microsoft Sentinel
New Exam SC-200 Study Guide
Are you looking for a guide on how to pass the SC-200 exam? You’ve come to the right place.
You can take advantage of Microsoft Learn to study for exams.
Read through all the topics on the Microsoft Learn learning path, and you’ll learn a lot.
You can use books to learn
The recommended ones here are:
- Exam Ref SC-200 Microsoft Security Operations Analyst
- Microsoft Security Operations Analyst Exam Ref SC-200 Certification Guide: Manage, monitor, and respond to threats using Microsoft Security Stack for securing IT systems
You can also use the SC-200 exam questions to study for the exam (currently the most effective)
You can go to Pass4itSure SC-200 exam questions practice materials to get new SC-200 exam questions to prepare for the exam (and it also has free SC-200 exam questions for you to try out). It is highly recommended that you combine reading, reading, and practice exam questions to study for the SC-200 exam.
Of course, there are many ways to study to prepare for exams, such as joining study groups, buying online courses, etc., which are all possible, and I mainly say the most cost-effective, direct and effective. You can combine these with the above to form your own unique and effective way of studying for the SC-200 exam, depending on your study habits.
Other Microsoft Azure Certification Guides…
Pass4itSure SC-200 Free Practice Exam Questions
Provided by the Pass4itSure website, contains 15 up-to-date exam questions, updated on May 22, 2024
Question 1:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You use Azure Security Center.
You receive a security alert in the Security Center.
You need to view recommendations to resolve the alert in the Security Center.
Solution: From Regulatory Compliance, you download the report.
Does this meet the goal?
A. Yes
B. No
Correct Answer: B
Question 2:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are configuring Azure Sentinel.
You need to create an incident in Azure Sentinel when a sign-in to an Azure virtual machine from a malicious IP address is detected.
Solution: You create a scheduled query rule for a data connector.
Does this meet the goal?
A. Yes
B. No
Correct Answer: B
Reference: https://docs.microsoft.com/en-us/azure/sentinel/connect-azure-security-center
Question 3:
You have an Azure subscription that uses Microsoft Defender for Cloud. You need to filter the security alerts view to show the following alerts:
1. An unusual user accessed a key vault
2. Log on from an unusual location
3. Impossible travel activity Which severity should you use?
A. Informational
B. Low
C. Medium
D. High
Correct Answer: C
Medium This is probably a suspicious activity that might indicate that a resource is compromised. Defender for Cloud\’s confidence in the analytic or finding is medium and the confidence of the malicious intent is medium to high. These would usually be machine learning or anomaly-based detections, for example, a sign-in attempt from an unusual location.
Incorrect:
*
High There is a high probability that your resource is compromised. You should look into it right away. Defender for Cloud has high confidence in both the malicious intent and in the findings used to issue the alert. For example, an alert detects the execution of a known malicious tool such as Mimikatz, a common tool used for credential theft.
*
Low This might be a benign positive or a blocked attack. Defender for Cloud isn’t confident enough that the intent is malicious and the activity might be innocent. For example, log clear is an action that might happen when an attacker tries to hide their tracks, but in many cases is a routine operation performed by admins. Defender for Cloud doesn’t usually tell you when attacks were blocked unless it\’s an interesting case that we suggest you look into.
*
Low This might be a benign positive or a blocked attack. Defender for Cloud isn’t confident enough that the intent is malicious and the activity might be innocent. For example, log clear is an action that might happen when an attacker tries to hide their tracks, but in many cases is a routine operation performed by admins. Defender for Cloud doesn’t usually tell you when attacks were blocked unless it\’s an interesting case that we suggest you look into.
Reference: https://learn.microsoft.com/en-us/azure/defender-for-cloud/alerts-overview
Question 4:
You have five on-premises Linux servers.
You have an Azure subscription that uses Microsoft Defender for Cloud.
You need to use Defender for Cloud to protect the Linux servers.
What should you install on the servers first?
A. The dependency agent
B. the Log Analytics agent
C. the Azure Connected Machine agent
D. the Guest Configuration extension
Correct Answer: B
Defender for Cloud depends on the Log Analytics agent. Use the Log Analytics agent if you need to:
*
Collect logs and performance data from Azure virtual machines or hybrid machines hosted outside of Azure
*
Etc.
Reference: https://docs.microsoft.com/en-us/azure/defender-for-cloud/os-coverage https://docs.microsoft.com/en-us/azure/azure-monitor/agents/agents-overview#log- analytics-agent
Question 5:
You have an Azure subscription that uses Microsoft Defender for Endpoint.
You need to ensure that you can allow or block a user-specified range of IP addresses and URLs.
What should you enable first in the advanced features from the Endpoints Settings in the Microsoft 365 Defender portal?
A. endpoint detection and response (EDR) in block mode
B. custom network indicators
C. web content filtering
D. Live response for servers
Correct Answer: B
Custom network indicators Configure devices to allow or block connections to IP addresses, domains, or URLs in your custom indicator lists. To use this feature, devices must be running Windows 10 version 1709 or later. They should also have network protection in block mode and version 4.18.1906.3 or later of the antimalware platform (see KB 4052623).
Note that network protection leverages reputation services that process requests in locations that might be outside of the location you have selected for your Microsoft Defender for Endpoint data.
Question 6:
HOTSPOT
You have a Microsoft 365 E5 subscription.
You plan to perform cross-domain investigations by using Microsoft 365 Defender.
You need to create an advanced hunting query to identify devices affected by a malicious email attachment.
How should you complete the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
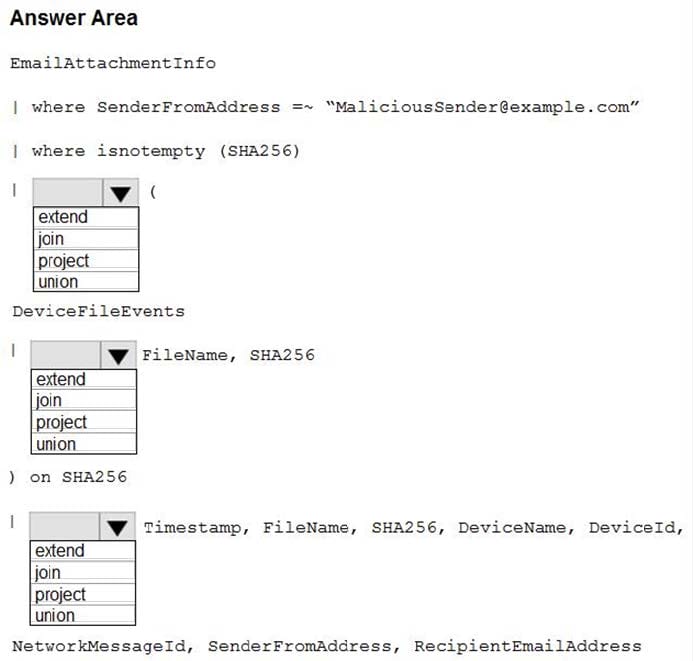
Correct Answer:
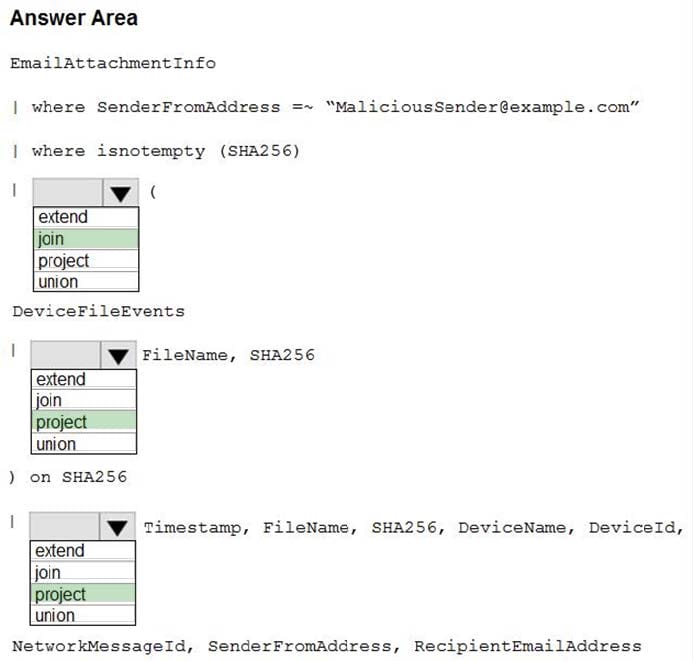
Question 7:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have Linux virtual machines on Amazon Web Services (AWS).
You deploy Azure Defender and enable auto-provisioning.
You need to monitor the virtual machines by using Azure Defender.
Solution: You manually install the Log Analytics agent on the virtual machines.
Does this meet the goal?
A. Yes
B. No
Correct Answer: B
Question 8:
HOTSPOT
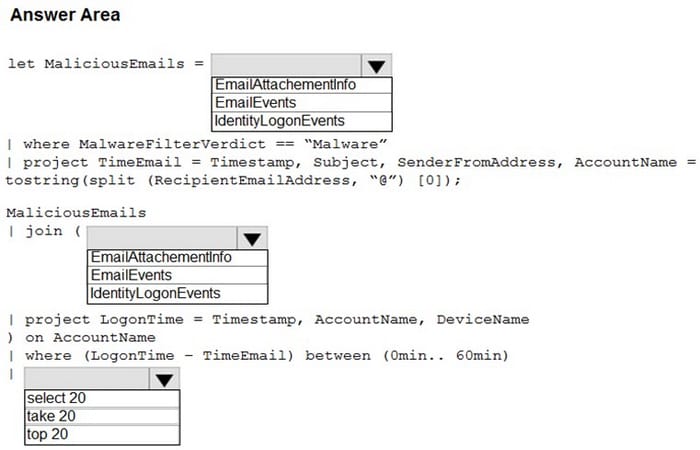
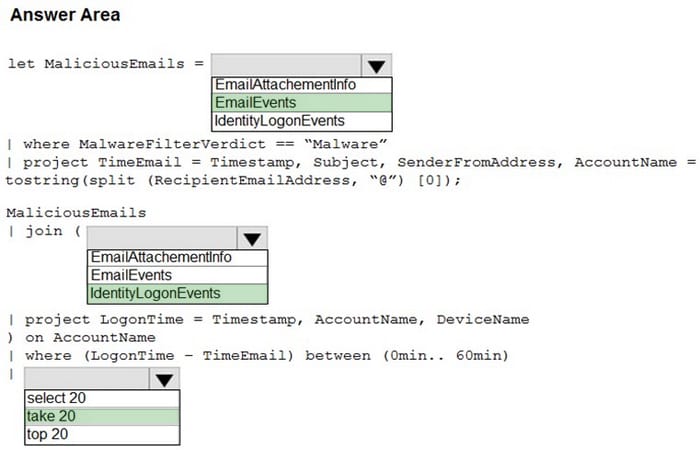
You are informed of an increase in malicious emails being received by users.
You need to create an advanced hunting query in Microsoft 365 Defender to identify whether the accounts of the email recipients were compromised. The query must return the most recent 20 sign-ins performed by the recipients within an hour of receiving the known malicious email.
How should you complete the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
Question 9:
DRAG DROP
You need to configure DC1 to meet the business requirements.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
Correct Answer:
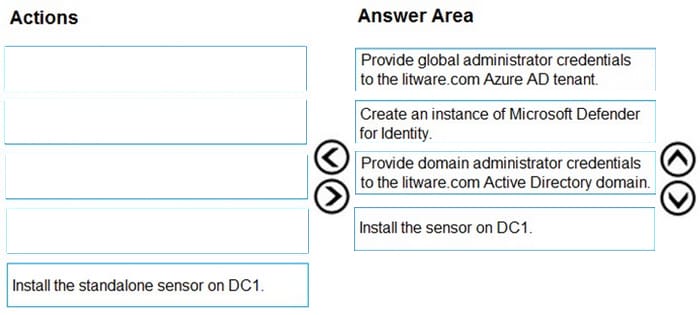
Step 1: log in to https://portal.atp.azure.com as a global admin Step 2: Create the instance Step 3. Connect the instance to Active Directory Step 4. Download and install the sensor.
Reference: https://docs.microsoft.com/en-us/defender-for-identity/install-step1 https://docs.microsoft.com/en-us/defender-for-identity/install-step4
Question 10:
You need to create the test rule to meet the Azure Sentinel requirements. What should you do when you create the rule?
A. From the Set rule logic, turn off suppression.
B. From Analytics rule details, configure the tactics.
C. From the Set rule logic, map the entities.
D. From Analytics rule details, configure the severity.
Correct Answer: C
Reference: https://docs.microsoft.com/en-us/azure/sentinel/tutorial-detect-threats-custom
Question 11:
You recently deployed Azure Sentinel.
You discover that the default Fusion rule does not generate any alerts. You verify that the rule is enabled.
You need to ensure that the Fusion rule can generate alerts.
What should you do?
A. Disable, and then enable the rule.
B. Add data connectors
C. Create a new machine learning analytics rule.
D. Add a hunting bookmark.
Correct Answer: B
Reference: https://docs.microsoft.com/en-us/azure/sentinel/connect-data-sources
Question 12:
You need to assign a role-based access control (RBAC) role to admin1 to meet the Azure Sentinel requirements and the business requirements. Which role should you assign?
A. Automation Operator
B. Automation Runbook Operator
C. Azure Sentinel Contributor
D. Logic App Contributor
Correct Answer: C
Litware must meet the following requirements:
- Ensure that a user named admin1 can configure Azure Sentinel playbooks.
2. The principle of least privilege must be used whenever possible.
Azure Sentinel Contributor can view data, incidents, workbooks, and other Azure Sentinel resources, manage incidents (assign, dismiss, etc.), and create and edit workbooks, analytics rules, and other Azure Sentinel resources.
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/roles
Question 13:
You have a Microsoft 365 subscription that uses Microsoft 365 Defender.
You need to identify all the entities affected by an incident.
Which tab should you use in the Microsoft 365 Defender portal?
A. Investigations
B. Devices
C. Evidence and Response
D. Alerts
Correct Answer: C
The Evidence and Response tab shows all the supported events and suspicious entities in the alerts in the incident.
Reference: https://docs.microsoft.com/en-us/microsoft-365/security/defender/investigate-incidents
Question 14:
DRAG DROP
You need to add notes to the events to meet the Azure Sentinel requirements.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
Correct Answer:
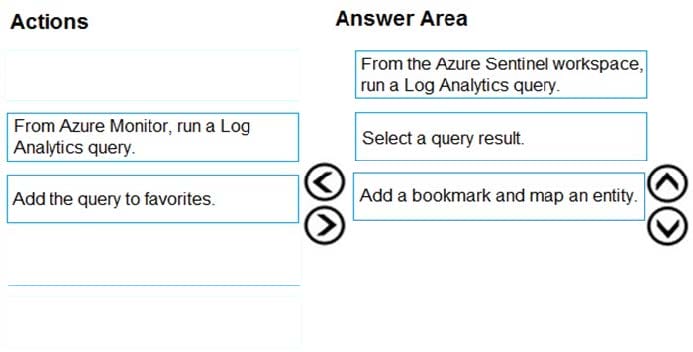
Reference: https://docs.microsoft.com/en-us/azure/sentinel/bookmarks
Question 15:
You have an Azure subscription that contains a Microsoft Sentinel workspace. The workspace contains a Microsoft Defender for Cloud data connector.
You need to customize which details will be included when an alert is created for a specific event.
What should you do?
A. Modify the properties of the connector.
B. Create a Data Collection Rule (DCR).
C. Create a scheduled query rule.
D. Enable User and Entity Behavior Analytics (UEBA)
Correct Answer: C
https://learn.microsoft.com/en-us/azure/sentinel/customize-alert-details
You can take practice tests multiple times to prepare for Microsoft Certified: Security Operations Analyst Associate. Feel relieved. These questions are reviewed by the Pass4itSure team of professionals and updated regularly.
With the Security Operations Analyst Associate certification, you will:
- Get a higher pay package
- Be more flexible and progressive in your career
- Improve your technical skills in the Azure cloud
Write at the end:
This blog does everything I hope will help you in studying for the Security Operations Analyst Associate SC-200 exam. Follow this guide to get https://www.pass4itsure.com/sc-200.html Pass4itSure SC-200 exam questions practice materials and you’re sure to pass the exam, get certified, and earn a great salary.
Here you can find free SC-200 exam questions, the new SC-200 study guide, and information about the latest SC-200 exams.

