Pass4itSure Microsoft 98-368 exam dumps are designed with the help of Microsoft’s real exam content. You can get 98-368 VCE dumps and 98-368 PDF dumps from Pass4itSure! Check out the best and updated 98-368 exam questions by Pass4itSure 98-368 dumps https://www.pass4itsure.com/98-368.html (Q&As: 66) (VCE and PDF), we are very confident that you will be successful on Microsoft 98-368 exam.
Microsoft 98-368 exam questions in PDF file
Download those Pass4itSure 98-368 pdf from Google Drive: https://drive.google.com/file/d/1-aFcLPHt1fyji7Lo9eiVWwWIjl6Dh3jy/view?usp=sharing
Microsoft MTA Certifications:
98-349: Windows Operating System Fundamentals
98-349 practice test free https://www.microsoft-technet.com/get-pass4itsure-microsoft-98-349-exam-dumps-as-practice-test-and-pdf.html
98-365: Windows Server Administration Fundamentals
98-365 practice test free https://www.microsoft-technet.com/get-pass4itsure-microsoft-98-365-exam-dumps-as-practice-test-and-pdf.html
98-367: Security Fundamentals
98-367 practice test free https://www.microsoft-technet.com/get-pass4itsure-microsoft-98-367-exam-dumps-as-practice-test-and-pdf.html
Following are some Microsoft 98-368 exam questions for review (Microsoft 98-368 practice test 1-13)
QUESTION 1
Your university\\’s IT department currently has no Active Directory strategy.
The university needs a solution that allows you to manage users and groups to secure access to Microsoft online
services such as Microsoft Office 365.
Which Active Directory strategy should the university use?
A. Active Directory Federation services
B. Active Directory Lightweight Directory services
C. Active Directory Certificate services
D. Azure Active Directory
Correct Answer: D
Azure Active Directory is preintegrated with Salesforce.com, Office 365, Box and many more.
QUESTION 2
You are using dual monitors on a Windows 8.1 computer. You want to move system tray to the secondary monitor.
Which Display option in Control Panel should you select?
A. Make this my main display
B. Landscape orientation
C. PC Screen only
D. Extend desktop to this display
Correct Answer: A
QUESTION 3
Which type of information about users does biometrics evaluate?
A. phrases a user has memorized
B. where a user is located
C. physical characteristics of a user
D. objects a user carries with him or her
Correct Answer: C
Biometrics refers to authentication techniques that rely on measurable physical characteristics that can be automatically
checked.
Note: There are several types of biometric identification schemes: face: the analysis of facial characteristics fingerprint:
the analysis of an individual\\’s unique fingerprints hand geometry: the analysis of the shape of the hand and the length
of the fingers retina: the analysis of the capillary vessels located at the back of the eye iris: the analysis of the colored
ring that surrounds the eye\\’s pupil signature: the analysis of the way a person signs his name. vein: the analysis of
pattern of veins in the back if the hand and the wrist voice: the analysis of the tone, pitch, cadence and frequency of a
person\\’s voice.
Reference: http://www.webopedia.com/TERM/B/biometrics.html
QUESTION 4
This question requires that you evaluate the underlined text to determine if it is correct.
In order to install Microsoft Intune client software on a computer, you need to be a member of that computer\\’s
“Administrators” group. Instructions: Review the underlined text. If it makes the statement correct, select “No change is
needed”. If
the statement is incorrect, select the answer choice than makes the statement correct.
A. No change is needed
B. Remote Management users
C. Power users
D. Remote Desktop users
Correct Answer: A
The account that installs the Intune client software must have local administrator permissions to that computer.
Reference: Requirements for Microsoft Intune https://technet.microsoft.com/en-us/library/dn646950.aspx
QUESTION 5
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct
selection is worth one point.
Hot Area:
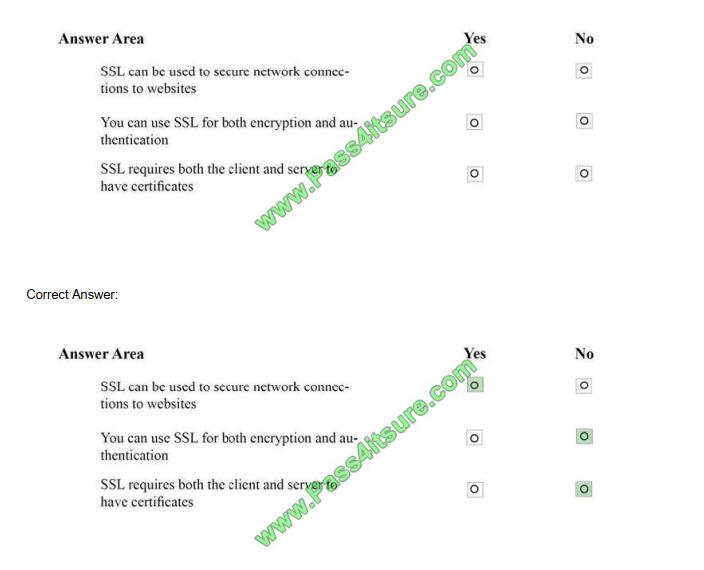
* Secure Sockets Layer (SSL) is a cryptographic protocol designed to provide communications security over a computer
network, such as secure connections to websites.
* SSL is used for encryption but not for authentication.
* There is SSL for the web server, but the client does not have a SSL certificate.
SSL Certificates are small data files that digitally bind a cryptographic key to an organization details.
When installed on a web server, it activates the padlock and the https protocol (over port 443) and allows secure
connections from a web server to a browser.
Reference: https://www.globalsign.com/en/ssl-information-center/what-is-an-ssl-certificate/
QUESTION 6
This question requires that you evaluate the underlined text to determine if it is correct.
If you need to make storage space available for an update on a Windows Phone 8.1 device, you should use “Action
Center” to move installed programs to and other data from the phone to the SD card. Instructions: Review the
underlined text.
If it makes the statement correct, select “No change is needed”. If the statement is incorrect, select the answer choice
than makes the statement correct.
A. No change is needed
B. File Explorer
C. Phone Update
D. Storage Sense
Correct Answer: D
To uninstall apps and games or move them to an SD card using Storage Sense
You can uninstall apps and games to free up space on your phone, or move them to an SD card (if you have one
installed).
1.
In the App list, go to Storage Sense Storage Sense Tile.
2.
Go to Phone > Apps+games.
3.
Tap an app or game file, and then tap Uninstall or Move to SD.
Reference: Make room on my phone to update it https://www.windowsphone.com/en-us/how-to/wp8/basics/make-roomon-my-phone-to-update-it
QUESTION 7
You want to use a Microsoft Account to log into devices on your home network.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Hot Area:
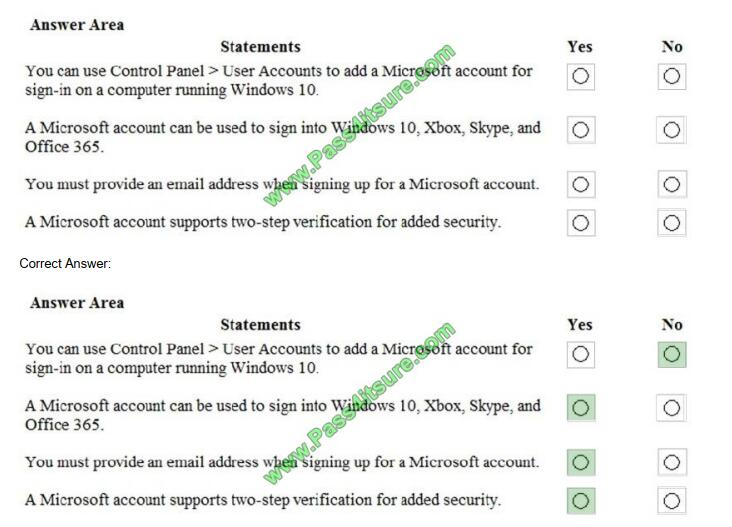
https://account.microsoft.com/account https://support.microsoft.com/en-us/help/12408/microsoft-account-how-to-usetwo-step-verification
QUESTION 8
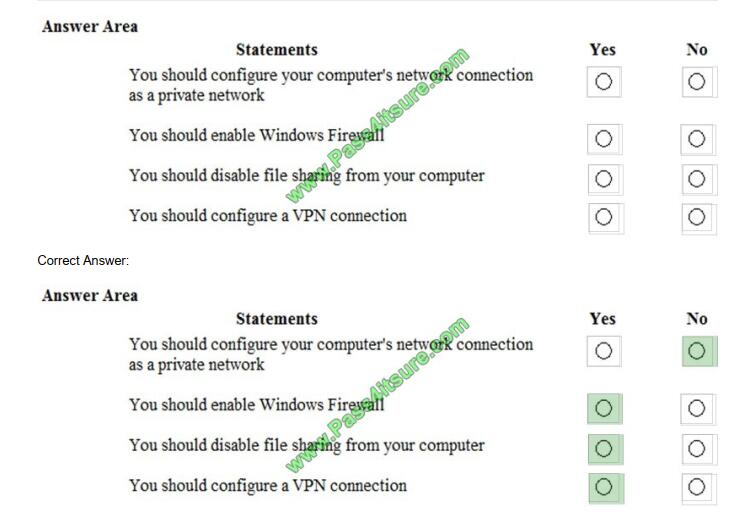
You use a laptop running Microsoft Windows 10. You connect to the Internet using the Wi-Fi connections at a coffee
shop.
You plan to visit several websites while doing a research project and want to verify that your computer is configured for
safe communication.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Hot Area:
https://thenextweb.com/insider/2015/08/08/how-to-stop-hackers-from-stealing-your-information-on-public-wi-fi/
https://www.lifewire.com/how-to-connect-to-a-wi-fi-network-2378229
QUESTION 9
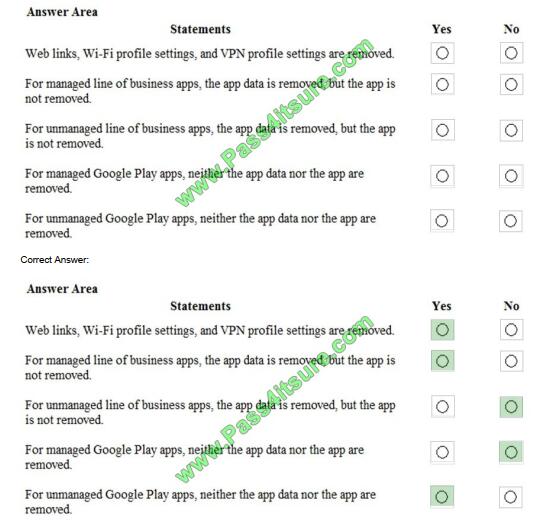
You perform a selective wipe on an Intune-managed Android device.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is
worth one point.
NOTE: Each correct selection is worth one point.
Hot Area:
https://docs.microsoft.com/en-us/intune/devices-wipe
QUESTION 10
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct
selection is worth one point.
Hot Area:
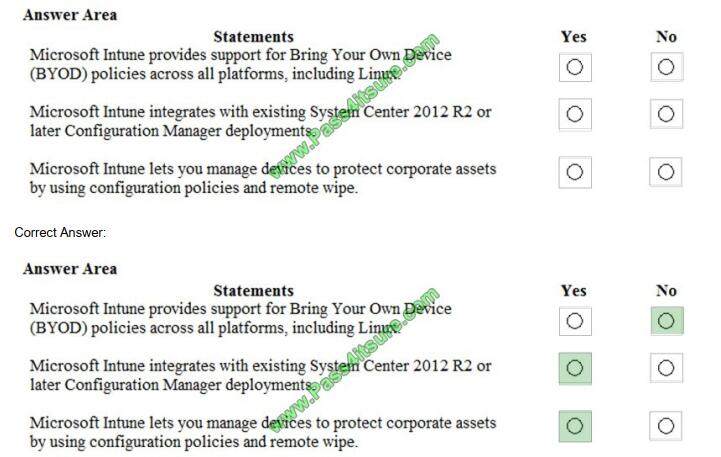
QUESTION 11
Which Microsoft cloud service can perform virtual video conferences?
A. Azure
B. Intune
C. Skype for Business
D. OneDrive
Correct Answer: C
References: https://www.skype.com/en/business/
https://www.lynda.com/SharePoint-tutorials/Microsoft-Cloud-Services-SharePoint-Online-OneDrive-Skype-BusinessOnline/618724-2.html
QUESTION 12
You need to create an Azure storage account through Azure Storage Services to support an Azure Windows virtual
machine (VM). You want to keep subscription costs to a minimum. What type of storage account should you create?
A. Standard storage performance tier
B. Blob cool access tier
C. Premium storage performance tier
D. Blob hot access tier
Correct Answer: D
References: https://www.petri.com/choosing-azure-storage-account-type
https://docs.microsoft.com/en-us/azure/storage/common/storage-introduction
QUESTION 13
What is an example of the way in which a Trojan horse commonly spreads to other computers?
A. It inserts copies of itself into other computer programs
B. It traverses a network by exploiting a vulnerability
C. It pretends to be a document from a friend
D. It downloads from an infected web page
Correct Answer: D
Trojan horses are commonly found on websites that offer free software, such as shareware programs. These communal
gathering spots on the Web give Trojan horse writers a degree of anonymity along with the chance of attacking as many
random victims as possible. Since website operators rarely have time to thoroughly examine every file posted, an
occasional Trojan horse can slip through the checking procedures unnoticed.
Reference: HOW TROJAN HORSES SPREAD http://etutorials.org/Misc/computer+book/Part+2+Dangerous+Threats+o
n+the+Internet/Chapter+8+Trojan+Horses-+Beware+of+Geeks+Bearing+Gifts/HOW+TROJAN+HORSES+SPREAD/
PS.
Thanks for reading! Hope the newest 98-368 exam dumps can help you in your exam. Get full 98-368 exam questions try Pass4itSure 98-368 dumps! 98-368 dumps in VCE and PDF are here: https://www.pass4itsure.com/98-368.html (Updated: Jun 20, 2021).
Download Pass4itSure 98-368 dumps pdf from Google Drive: https://drive.google.com/file/d/1-aFcLPHt1fyji7Lo9eiVWwWIjl6Dh3jy/view?usp=sharing (98-368 Exam Questions)