
Reliable Microsoft MD-102 dumps help you open the door to your career. Take advantage of the victory today!
Enhance your Endpoint Administrator exam preparation capabilities: Succeed with reliable MD-102 dumps and well-designed MD-102 exam practice questions.
Download the reliable MD-102 dumps and up-to-date MD-102 questions now at https://www.pass4itsure.com/md-102.html with a PDF or VCE to pave the way for your test success.
Review the new MD-102 information to help you prepare for the exam
The English version of the MD-102 exam was updated on November 1, 2023. Therefore, you must update the new exam information to cope with the exam.
The MD-102 exam is an endpoint administrator certification exam that requires expertise in deploying, configuring, securing, managing, and monitoring devices and client applications in a Microsoft 365 environment. The duration of the exam is 120 minutes, with 40-60 questions (multiple choice and multiple answers) and a passing score of 700 out of 1000.
Comparison between the old and new versions of the MD-102 exam skill measures:
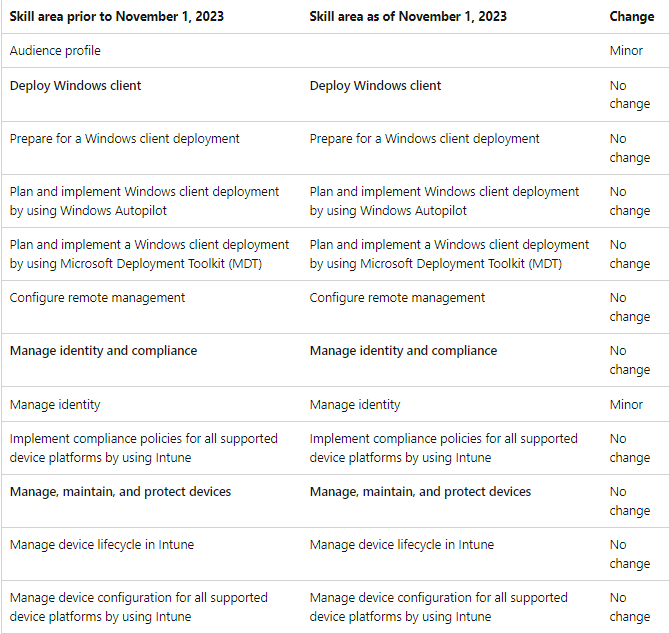
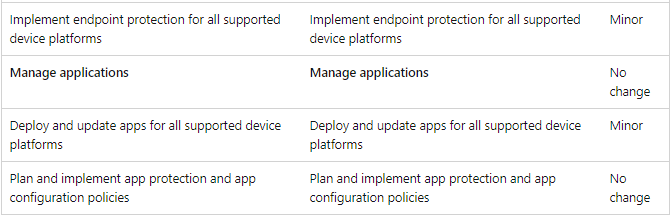
Share some new MD-102 dumps exam questions free online practice:
From: Pass4itSure | Many exam questions: 15 | Associated certification: Microsoft 365
Question 1:
You use Windows Admin Center to remotely administer computers that run Windows 10.
When connecting to Windows Admin Center, you receive the message shown in the following exhibit.
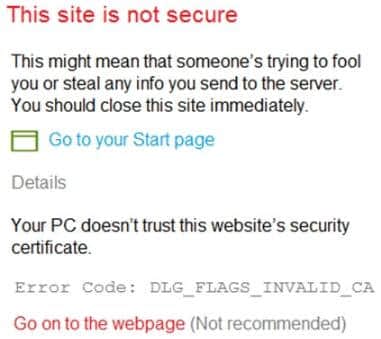
You need to prevent the message from appearing when you connect to the Windows Admin Center. To which certificate store should you import the certificate?
A. Client Authentication Issuers
B. Personal
C. Trusted Root Certification Authorities
Correct Answer: C
Explanation:
“Error Code: DLG_FLAGS_INVALID_CA” while logging to Admin Console after enabling HTTPS in PowerCenter.
Solution
To resolve this issue, add the CA-signed certificates to the “Trusted Root Certification Authorities” in the browser. After adding the certificates, restart the browser.
Reference:
https://knowledge.informatica.com/s/article/578585
Question 2:
You use Microsoft Defender for Endpoint to protect computers that run Windows 10.
You need to assess the differences between the configuration of Microsoft Defender for Endpoint and the Microsoft-recommended configuration baseline.
Which tool should you use?
A. Microsoft Defender for Endpoint Power BI app
B. Microsoft Secure Score
C. Endpoint Analytics
D. Microsoft 365 Defender portal
Correct Answer: D
Explanation:
Security baselines assessment
A security baseline profile is a customized profile that you can create to assess and monitor endpoints in your organization against industry security benchmarks. When you create a security baseline profile, you\’re creating a template that
consists of multiple device configuration settings and a base benchmark to compare against.
Get started with security baselines assessment
1. Go to Vulnerability Management> Baselines assessment in the Microsoft 365 Defender portal.
2. Select the Profiles tab at the top, then select the Create profile button.
3. Enter a name and description for your security baseline profile and select Next.
4. On the Baseline profile scope page set the profile settings such as software, base benchmark (CIS or STIG), and the compliance level and select Next.
5. Select the configurations you want to include in the profile.
6. Select Next to choose the device groups and device tags you want to include in the baseline profile. The profile will be automatically applied to devices added to these groups in the future.
7. Select Next to review the profile.
8. Select Submit to create your profile.
9. On the final page, select View profile page to see the assessment results.
Reference:
Question 3:
Your network contains an Active Directory domain. The domain contains a computer named Computer1 that runs Windows 11. You need to enable the Windows Remote Management (WinRM) service on Computer1 and perform the following configurations: For the WinRM service, set the Startup type to Automatic.
Create a listener that accepts requests from any IP address. Enable a firewall exception for management communications. Which PowerShell cmdlet should you use?
A. Connect-WSMan
B. Enable-PSRemoting
C. Invoke-WSManAction
D. Enable-PSSessionConfiguration
Correct Answer: B
Explanation:
The Enable-PSRemoting cmdlet configures the computer to receive PowerShell remote commands that are sent by using the WS-Management technology. WS-Management-based PowerShell remoting is currently supported only on
Windows platform.
The Enable-PSRemoting cmdlet performs the following operations:
* Runs the Set-WSManQuickConfig cmdlet, which performs the following tasks:
Starts the WinRM service.
Sets the startup type on the WinRM service to Automatic.
Creates a listener to accept requests on any IP address.
Enables a firewall exception for WS-Management communications.
Creates the simple and long name session endpoint configurations if needed.
Enables all session configurations.
Changes the security descriptor of all session configurations to allow remote access.
* Restarts the WinRM service to make the preceding changes effective.
Reference:
https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.core/enable-psremoting
Question 4:
You need to prepare for the deployment of the Phoenix office computers.
What should you do first?
A. Generalize the computers and configure the Device settings from the Microsoft Entra admin center.
B. Extract the serial number of each computer to an XML file and upload the file from the Microsoft Intune admin center.
C. Extract the hardware ID information of each computer to a CSV file and upload the file from the Microsoft Intune admin center.
D. Generalize the computers and configure the Mobility (MDM and MAM) settings from the Microsoft Entra admin center.
E. Extract the serial number information of each computer to a CSV file and upload the file from the Microsoft Intune admin center.
Correct Answer: C
Explanation:
To manage devices through Microsoft Store for Business and Education, you\’ll need a .csv file that contains specific information about the devices. You should be able to get this from your Microsoft account contact, or the store where you purchased the devices. Upload the .csv file to Microsoft Store to add the devices.
Note:
Provide new computers to the Phoenix office users. The new computers have Windows 10 Pro preinstalled and were purchased already.
Deploy Windows 10 Enterprise to the computers of the Phoenix office users by using Windows Autopilot.
Reference:
https://docs.microsoft.com/en-us/microsoft-store/add-profile-to-devices
Question 5:
You have a Microsoft 365 subscription that uses Microsoft Intune Suite.
You use Microsoft Intune to manage devices.
You need to ensure that the startup performance of managed Windows 11 devices is captured and available for review in the Intune admin center.
What should you configure?
A. the Azure Monitor agent
B. a device compliance policy
C. a Conditional Access policy
D. an Intune data collection policy
Correct Answer: A
Explanation:
What is the Azure Monitor Agent?
Azure Monitor Agent (AMA) collects monitoring data from the guest operating system of Azure and hybrid virtual machines and delivers it to Azure Monitor for use by features, insights, and other services, such as Microsoft Sentinel and
Microsoft Defender for Cloud.
Incorrect:
Not D:
An Intune data collection policy collects user experience data.
Reference:
https://learn.microsoft.com/en-us/azure/azure-monitor/agents/agents-overview
Question 6:
You have a Microsoft 365 E5 subscription and 100 unmanaged iPad devices.
You need to deploy a specific iOS update to the devices. Users must be prevented from manually installing a more recent version of iOS.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Create a device configuration profile.
B. Enroll the devices in Microsoft Intune by using the Intune Company Portal.
C. Create a compliance policy.
D. Create an iOS app provisioning profile.
E. Enroll the devices in Microsoft Intune by using Apple Business Manager.
Correct Answer: AE
Explanation:
A: iOS and iPadOS device settings to allow or restrict features using Intune
There are different settings you can control on iOS and iPad devices. As part of your mobile device management (MDM) solution, use these settings to allow or disable features, set password rules, allow or restrict specific apps, and more.
This feature applies to:
iOS/iPad
These settings are added to a device configuration profile in Intune and then assigned or deployed to your iOS/iPad devices.
E: Enroll iOS and iPadOS devices in Microsoft Intune
Personal and organization-owned devices can be enrolled in Intune. Once they\’re enrolled, they receive the policies and profiles you create. You have the following options when enrolling iOS/iPadOS devices:
Automated device enrollment (ADE)
Apple Configurator
BYOD: User and Device enrollment
Automated Device Enrollment (ADE) (supervised)
Previously called the Apple Device Enrollment Program (DEP). Use on devices owned by your organization. This option configures settings using Apple Business Manager (ABM) or Apple School Manager (ASM). It enrolls a large number of devices, without you ever touching the devices. These devices are purchased from Apple, have your preconfigured settings, and can be shipped directly to users or schools. You create an enrollment profile in the Intune admin center and push this profile to the devices.
Reference:
https://learn.microsoft.com/en-us/mem/intune/configuration/device-restrictions-ios
https://learn.microsoft.com/en-us/mem/intune/fundamentals/deployment-guide-enrollment-ios-ipados
Question 7:
You have an on-premises server named Server1 that hosts a Microsoft Deployment Toolkit (MDT) deployment share named MDT1.
You need to ensure that MDT1 supports multicast deployments.
What should you install on Server1?
A. Multipath I/O (MPIO)
B. Multipoint Connector
C. Windows Deployment Services (WDS)
D. Windows Server Update Services (WSUS)
Correct Answer: C
Explanation:
Multicast requires that Windows Deployment Services (WDS) is running on Windows Server 2008 or later.
Reference:
Question 8:
You have a Microsoft 365 E5 subscription that contains the devices shown in the following table.
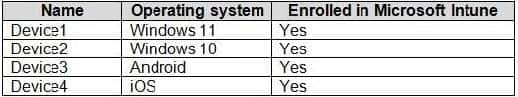
All devices have Microsoft Edge installed.
From the Microsoft Intune admin center, you create a Microsoft Edge Baseline profile named Edge1.
You need to apply Edge1 to all the supported devices.
To which devices should you apply Edge1?
A. Device1 only
B. Device1 and Device2 only
C. Device1, Device2, and Device3 only
D. Device1, Device2, and Device4 only
E. Device1, Device2, Device3, and Device4
Correct Answer: B
Explanation:
Windows 10 and Windows 11 only.
Reference:
https://learn.microsoft.com/en-us/mem/intune/protect/security-baseline-settings-edge
Question 9:
You have a Microsoft 365 subscription that uses Microsoft Intune Suite.
You use Microsoft Intune to manage devices.
You use Windows Autopilot to deploy Windows 11 to devices.
A support engineer reports that when a deployment fails, they cannot collect deployment logs from failed devices.
You need to ensure that when a deployment fails, the deployment logs can be collected.
What should you configure?
A. the automatic enrollment settings
B. the Windows Autopilot deployment profile
C. the enrollment status page (ESP) profile
D. the device configuration profile
Correct Answer: C
Explanation:
Troubleshooting the Enrollment Status Page
To troubleshoot ESP issues, it\’s important to get more information about the ESP settings that are received by the device, and the applications and policies that are tracked at each stage. All ESP settings and tracking information are logged in the device registry.
Collect logs
You can enable the ability for users to collect ESP logs in the ESP policy. When a timeout occurs in the ESP, the user can select the option to Collect logs.
Note: Windows Autopilot diagnostics page
On Windows 11, you can open the Autopilot diagnostic page to view additional detailed troubleshooting information about the Autopilot provisioning process. To enable the Autopilot diagnostics page:
Go to the ESP profile where the Autopilot diagnostics page needs to be enabled.
Make sure that Show app and profile configuration progress is selected to Yes.
Make sure that the turn-on log collection and diagnostics page for end users is selected to Yes.
Reference:
Question 10:
You have a Microsoft 365 subscription that contains a user named User1 and uses Microsoft Intune Suite.
You use Microsoft Intune to manage devices that run Windows 11.
The user provides remote support for 75 devices in the marketing department.
You need to add User1 to the Remote Desktop Users group on each marketing department device.
What should you configure?
A. an app configuration policy
B. a device compliance policy
C. an account protection policy
D. a device configuration profile
Correct Answer: B
Explanation:
Add users to Remote Desktop Users group
Remote Desktop Users group is used to grant users and groups permission to remotely connect to the device. Users can be added either manually or through MDM policies:
*Adding users manually
*Adding users using policy: Starting in Windows 10, version 2004, you can add users to the Remote Desktop Users using MDM policies Note 1: A Mobile Device Management (MDM) policy is a set of rules that establish how employees can and should securely use mobile devices. A mobile device management policy covers securing data in laptops, smartphones (either iOS or
Android), tablets, and portable media devices.
Note 2: Mobile device management (MDM) solutions like Intune can help protect organizational data by requiring users and devices to meet some requirements. In Intune, this feature is called compliance policies.
Reference:
https://learn.microsoft.com/en-us/windows/client-management/client-tools/connect-to-remote-aadj-pc https://learn.microsoft.com/en-us/mem/intune/protect/device-compliance-get-started
Question 11:
You have a computer named Computer1 that runs Windows 11.
A user named User1 plans to use Remote Desktop to connect to Computer1.
You need to ensure that the device of User1 is authenticated before the Remote Desktop connection is established and the sign-in page appears.
What should you do on Computer1?
A. Turn on Reputation-based protection
B. Enable Network Level Authentication (NLA)
C. Turn on Network Discovery
D. Configure the Remote Desktop Configuration service
Correct Answer: B
Explanation:
What is Network Level Authentication?
Network-level authentication is used for authenticating Remote Desktop services, such as Windows RDP, and Remote Desktop Connection (RDP Client). You might also hear it called front authentication.
What is Network Level Authentication (NLA) used for?
Before you can start a remote desktop session, the user will need to authenticate themselves – ie, prove that they are who they say they are. Using network-level authentication means that a false connection can’t be made, which would use up the CPU and cause a strain on the resources of the network. This offers a level of security against some cyberattacks such as Denial of Service attacks, where multiple requests are made all at once towards a network, overwhelming its ability to cope. To combat this, you can turn on network-level authentication to authenticate the user\’s credentials before starting a remote access session. If the user\’s credentials aren’t authenticated, then the connection is simply denied.
Reference: https://www.atera.com/blog/what-is-network-level-authenticatio
Question 12:
You install a feature update on a computer that runs Windows 10. How many days do you have to roll back the update?
A. 5
B. 10
C. 14
D. 30
Correct Answer: B
Explanation:
Microsoft has changed the period associated with operating system rollbacks with Windows 10 version 1607, decreasing it to 10 days. Previously, Windows 10 had a 30-day rollback period.
Reference:
https://redmondmag.com/articles/2016/08/04/microsoft-shortens-windows-10-rollback-period.aspx
Question 13:
You have a Microsoft 365 E5 subscription that contains a user named User1 and uses Microsoft Intune Suite.
You use Microsoft Intune to manage devices.
You have a device named Devic1 that is enrolled in Intune.
You need to ensure that User1 can use Remote Help from the Intune admin center for Device1.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Deploy the Remote Help app to Device 1.
B. Assign the Help Desk Operator role to User1.
C. Assign the Intune Administrator role to User1.
D. Assign a Microsoft 365 E5 license to User1.
E. Rerun device onboarding on Device1.
F. Assign the Remote Help add-on license to User1.
Correct Answer: ABE
Explanation:
Use Remote Help with Microsoft Intune
Prerequisites
Intune subscription
*-> (E) Remote Help add-on license or an Intune Suite license for all IT support workers (helpers) and users (sharers)
Windows 10/11
*-> (A) The Remote Help app for Windows.
Remote Help is available as a download from Microsoft and must be installed on each device before that device can be used to participate in a Remote Help session.
Configure Remote Help for your tenant
To configure your tenant to support Remote Help, review and complete the following tasks.
Task 1 – Enable Remote Help
(B) Task 2 – Configure permissions for Remote Help
The following Intune RBAC permissions manage the use of the Remote Help app. Set each to Yes to grant the permission:
Category: Remote Help app Permissions: Take full control – Yes/No Elevation – Yes/No View screen – Yes/No By default, the built-in Help Desk Operator role sets all of these permissions to Yes. You can use the built-in role or create custom roles to grant only the remote tasks and Remote Help app permissions that you want different groups of users to have.
Reference: https://learn.microsoft.com/en-us/mem/intune/fundamentals/remote-help
Question 14:
You have 100 computers that run Windows 10 and connect to an Azure Log Analytics workspace.
Which three types of data can you collect from the computers by using Log Analytics? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. failure events from the Security log
B. the list of processes and their execution times
C The average processor utilization
D. error events from the System log
E. third-party application logs stored as text files
Correct Answer: CDE
Explanation:
E: The Custom Logs data source for the Log Analytics agent in Azure Monitor allows you to collect events from text files on both Windows and Linux computers. Many applications log information to text files instead of standard logging services, such as Windows Event log or Syslog. After the data is collected, you can either parse it into individual fields in your queries or extract it during collection to individual fields.
D: Collect Windows event log data sources with Log Analytics agent Windows event logs are one of the most common data sources for Log Analytics agents on Windows virtual machines because many applications write to the Windows event log. You can collect events from standard logs, such as System and Application, and any custom logs created by applications you need to monitor.
C: Summary of data sources The following table lists the agent data sources that are currently available with the Log Analytics agent. Each agent data source links to an article that provides information for that data source. It also provides information on their method and frequency of collection.
*Performance counters Performance counters in Windows and Linux provide insight into the performance of hardware components, operating systems, and applications. Azure Monitor can collect performance counters from Log Analytics agents at frequent intervals for near real-time analysis. Azure Monitor can also aggregate performance data for longer-term analysis and reporting.
*Etc.
Log queries with performance records The following table provides different examples of log queries that retrieve performance records. Example, CPU utilization across all computers Query: Perf | where ObjectName == “Processor” and CounterName == “% Processor Time” and InstanceName == “_Total” | summarize AVGCPU = avg(CounterValue) by Computer Average
B: The following table lists the objects and counters that you can specify in the configuration file. More counters are available for certain applications.
*Processor, % Processor Time
*Processor, % User Time
*Etc.
Incorrect:
Not A: Not from the Security log.
Important
You can’t configure the collection of security events from the workspace by using the Log Analytics agent. You must use Microsoft Defender for Cloud or Microsoft Sentinel to collect security events. The Azure Monitor agent can also be used to collect security events.
Reference: https://learn.microsoft.com/en-us/azure/azure-monitor/agents/data-sources-custom-logs https://learn.microsoft.com/en-us/azure/azure-monitor/agents/data-sources-windows-events https://learn.microsoft.com/en-us/azure/azure-monitor/agents/data-sources-performance-counters
Question 15:
Your company has a wireless access point that uses WPA2-Enterprise. You need to configure a computer to connect to the wireless access point. What should you do first?
A. Create a provisioning package in Windows Configuration Designer.
B. Request a passphrase.
C. Request and install a certificate.
D. Create a Connection Manager Administration Kit (CMAK) package.
Correct Answer: B
Reference: https://support.microsoft.com/en-za/help37/windows-setting-up-wireless-network
May ask:
MD-102 Is the exam as difficult to pass as the legend says?
Yes, the Microsoft 365 MS-102 exam is professional and difficult. But with reliable MD-102 dumps study materials, it will be easy to pass.
What is the purpose of the MD-102 exam?
The MD-102 exam is associated with the Microsoft 365 Certified: Modern Desktop Administrator Associate certification. Then the purpose of the exam is definitely to help you get this certification and prove your ability.
What resources are available to prepare for the MD-102 exam?
In addition to what I’ve shared above, you can learn in the following resources:
- Choose from self-paced learning paths and modules or take an instructor-led course
- Windows Documentation
- Windows client documentation for IT Pros
- Configure Windows client
- Windows client deployment resources and documentation
- Manage Windows client
- Windows Security
- Windows Autopilot documentation
- Microsoft Intune documentation
- Microsoft Endpoint Manager documentation
- Windows application management
- Windows – Microsoft Tech Community
- Microsoft Learn – Microsoft Tech Community
- Exam Readiness Zone
Speaking of which, go ahead and share the MD-102 exam books, Just to help you pass the MD-102 exam.
Some good books about the MD-102 exam that will help with the exam:
- Mastering Microsoft 365 Administration
- Professional Microsoft 365 Administration
- Microsoft Office 365 Administration Inside Out
That’s all for sharing, if you want to see more Microsoft certification exam sharing, please lock Microsoft-technet.com!
Well, to sum it up:
If you want to succeed in the Microsoft 365 Certified: Endpoint Administrator Associate exam, you must get reliable MD-102 dumps, and we here at Pass4itSure provide you with the most reliable MD-102 exam practice questions 250+
(PDF or VCE) https://www.pass4itsure.com/md-102.html must lead you to exam success.
Admittedly, the path to passing the Microsoft MD-102 exam is rigorous and also requires your unwavering dedication and thorough preparation.
