Pass4itSure’s team of Microsoft experts has updated the SC-200 dumps with 111 questions and answers, making it the most effective Microsoft Security Operations Analyst learning material.
Click the URL to enter the Microsoft SC-200 dumps page: https://www.pass4itsure.com/sc-200.html These questions and answers are beneficial for preparing for your Microsoft SC-200 exam.
New SC-200 dumps, the best study material for preparing for the Microsoft Security SC-200 exam.
Should studying for an SC-200 exam start with the basics?
Yes, you have to start by being clear about the Microsoft sc-200 exam basics.
Exam SC-200: Microsoft Security Operations Analyst
Abbreviation: SC-200
Full name: Microsoft Security Operations Analyst
Languages: English, Japanese, Chinese (Simplified), Korean, French, German, Spanish, Portuguese (Brazil), Russian, Arabic (Saudi Arabia), Chinese (Traditional), Italian, Indonesian (Indonesia)
Exam duration: 120 minutes
Exam Fees: Price based on proctoring country
Passing score: 700 (1-1000)
Microsoft SC-200 Exam Topics: Mitigating Threats with Microsoft 365 Defender; Use Microsoft Defender for Cloud to mitigate threats; Use Microsoft Sentinel to mitigate threats
Certification: Microsoft Certified: Security Operations Analyst Associate
Pass: You may be eligible for ACE University credit
How do you get Microsoft Certified: Security Operations Analyst Associate?
The Microsoft Certified: Security Operations Analyst Associate certification is associated with the SC-200 exam and can be earned by successfully passing the SC-200 exam.
Want Microsoft Role-based SC-200 exam resources?
As shown below,
Of course the above are all official, if you want other free resources, keep reading.
Read Microsoft Security Operations Analyst Learning SC-200 free dumps Q&A:
QUESTION # 1
You need to modify the anomaly detection policy settings to meet the Cloud App Security requirements. Which policy should you modify?
A. Activity from suspicious IP addresses
B. Activity from anonymous IP addresses
C. Impossible travel
D. Risky sign-in
Correct Answer: C
Reference: https://docs.microsoft.com/en-us/cloud-app-security/anomaly-detection-policy
QUESTION # 2
You need to create the test rule to meet the Azure Sentinel requirements. What should you do when you create the rule?
A. From Set rule logic, turn off suppression.
B. From Analytics rule details, configure the tactics.
C. From Set rule logic, map the entities.
D. From Analytics rule details, configure the severity.
Correct Answer: C
Reference: https://docs.microsoft.com/en-us/azure/sentinel/tutorial-detect-threats-custom
QUESTION # 3
DRAG DROP
You are informed of a new common vulnerabilities and exposures (CVE) vulnerability that affects your environment. You need to use Microsoft Defender Security Center to request remediation from the team responsible for the affected systems if there is a documented active exploit available.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:

QUESTION # 4
You have a Microsoft 365 subscription that uses Azure Defender
You have 100 virtual machines in a resource group named RG1.
You assign the Security Admin roles to a new user named SecAdmin1.
You need to ensure that SecAdmin1 can apply quick fixes to the virtual machines by using Azure Defender. The solution must use the principle of least privilege.
Which role should you assign to SecAdmin1?
A. the Security Reader role for the subscription
B. the Contributor for the subscription
C. the Contributor role for RG1
D. the Owner role for RG1
Correct Answer: C
QUESTION # 5
You need to visualize Azure Sentinel data and enrich the data by using third-party data sources to identify indicators of compromise (IoC). What should you use?
A. notebooks in Azure Sentinel
B. Microsoft Cloud App Security
C. Azure Monitor
D. hunting queries in Azure Sentinel
Correct Answer: A
Reference: https://docs.microsoft.com/en-us/azure/sentinel/notebooks
QUESTION # 6
HOTSPOT
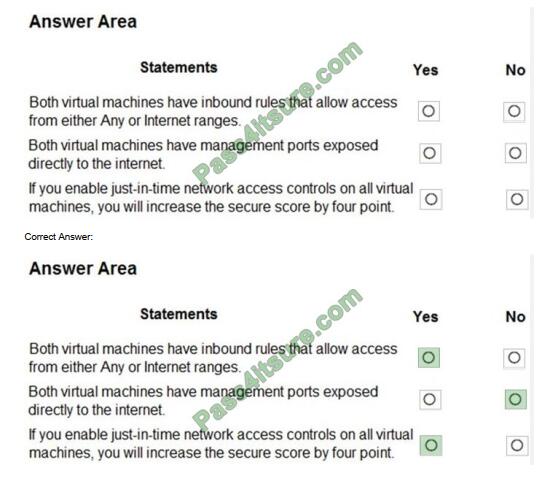
You manage the security posture of an Azure subscription that contains two virtual machines name vm1 and vm2. The secure score in Azure Security Center is shown in the Security Center exhibit. (Click the Security Center tab.) Azure Policy assignments are configured as shown in the Policies exhibit. (Click the Policies tab.) For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
QUESTION # 7
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You use Azure Security Center. You receive a security alert in Security Center. You need to view recommendations to resolve the alert in Security Center.
Solution: From Security alerts, you select the alert, select Take Action, and then expand the Mitigate the threat section. Does this meet the goal?
A. Yes
B. No
Correct Answer: A
QUESTION # 8
The issue for which team can be resolved by using Microsoft Defender for Endpoint?
A. executive
B. sales
C. marketing
Correct Answer: B
QUESTION # 9
DRAG DROP
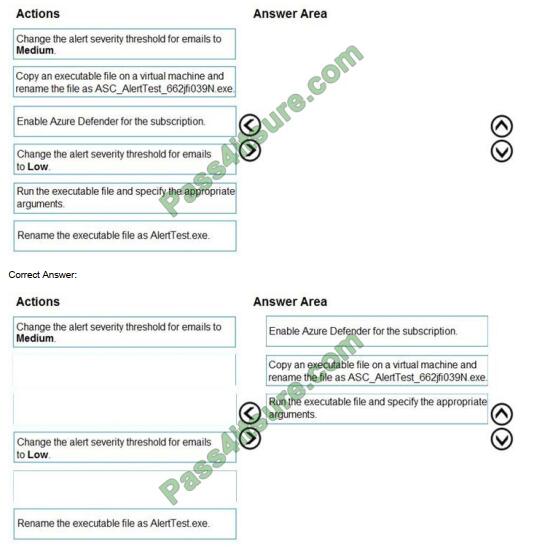
You create a new Azure subscription and start collecting logs for Azure Monitor. You need to configure Azure Security Center to detect possible threats related to sign-ins from suspicious IP addresses
to Azure virtual machines. The solution must validate the configuration.
Which three actions should you perform in a sequence? To answer, move the appropriate actions from the list of action to the answer area and arrange them in the correct order.
Select and Place:
QUESTION # 10
Your company stores the data for every project in a different Azure subscription. All the subscriptions use the same Azure Active Directory (Azure AD) tenant.
Every project consists of multiple Azure virtual machines that run Windows Server. The Windows events of the virtual machines are stored in a Log Analytics workspace in each machine\\’s respective subscription.
You deploy Azure Sentinel to a new Azure subscription.
You need to perform hunting queries in Azure Sentinel to search across all the Log Analytics workspaces of all the subscriptions. Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Add the Security Events connector to the Azure Sentinel workspace.
B. Create a query that uses the workspace expression and the union operator.
C. Use the alias statement.
D. Create a query that uses the resource expression and the alias operator.
E. Add the Azure Sentinel solution to each workspace.
Correct Answer: BE
Reference: https://docs.microsoft.com/en-us/azure/sentinel/extend-sentinel-across-workspaces-tenants
QUESTION # 11
HOTSPOT
From Azure Sentinel, you open the Investigation pane for a high-severity incident as shown in the following exhibit.
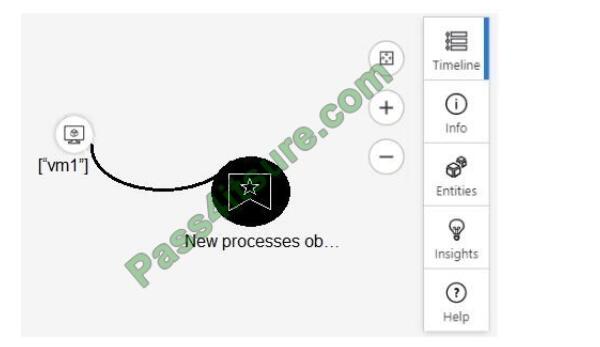
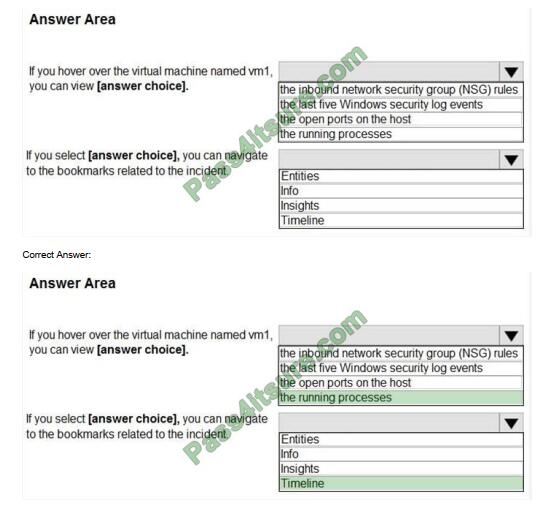
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
Hot Area:
QUESTION # 12
You have a custom analytics rule to detect threats in Azure Sentinel.
You discover that the analytics rule stopped running. The rule was disabled, and the rule name has a prefix of AUTO DISABLED. What is a possible cause of the issue?
A. There are connectivity issues between the data sources and Log Analytics.
B. The number of alerts exceeded 10,000 within two minutes.
C. The rule query takes too long to run and times out.
D. Permissions to one of the data sources of the rule query were modified.
Correct Answer: D
Reference: https://docs.microsoft.com/en-us/azure/sentinel/tutorial-detect-threats-custom
QUESTION # 13
You are investigating a potential attack that deploys a new ransomware strain.
You plan to perform automated actions on a group of highly valuable machines that contain sensitive information. You have three custom device groups. You need to be able to temporarily group the machines to perform actions on the devices.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Add a tag to the device group.
B. Add the device users to the admin role.
C. Add a tag to the machines.
D. Create a new device group that has a rank of 1.
E. Create a new admin role.
F. Create a new device group that has a rank of 4.
Correct Answer: BDE
Reference: https://www.drware.com/how-to-use-tagging-effectively-in-microsoft-defender-for-endpoint-part-1/
For more full SC-200 dumps question answers, this website.
Download free SC-200 dumps questions and answers: https://drive.google.com/file/d/1WP6EEEBM58rFjBrqPV0q2rD1FAICIxCa/view?usp=sharing