
When it comes to passing the Microsoft Certified: Security, Compliance, and Identity Fundamentals exam, you can’t miss it without the help of Microsoft SC-900 exam questions, and here we share the latest Microsoft SC-900 exam questions and discuss the key factors for achieving exam success.
Introduce
To study for an exam, you must first understand it.
What is: The SC-900 exam is the only exam required to earn Microsoft Certified: Security, Compliance, and Identity Fundamentals and an optional exam in security, compliance, and the identity path.
Learning to follow the path: Prepare for the exam – Find study resources – Practice for the exam – Take the exam
How to tell if you’re a good fit for the exam: Start by asking yourself two questions: 1. Do you want to be familiar with cloud-based security, compliance, and identity (SCI) fundamentals for Microsoft services? 2. Are you interested in Microsoft SCI solutions? If the answer is “yes,” then the SC-900 exam is for you.
The SC-900 exam can be aimed: at business stakeholders, new or existing IT professionals, students
Exam skills: that describe the concepts of security, compliance, and identity, the capabilities of Microsoft Entra, the capabilities of Microsoft security solutions, and the capabilities of Microsoft compliance solutions
Exam duration: 45 minutes
Test languages: English, Japanese, Chinese (Simplified), Korean, French, Spanish, Portuguese (Brazil), Russian, Arabic (Saudi Arabia), Indonesian (Indonesia), German, Chinese (Traditional), Italian
Cost: $99
How many questions: 40-60 questions
How to take the exam: Register through Pearson Vue or Certiport
Factors for Exam Success 1: (Cybersecurity, Compliance, and Microsoft Technologies) Industry Trends
After understanding the exam, it is not enough. Follow industry trends to achieve high scores.
The SC-900 exam is about Microsoft Certified: Security, Compliance, and Identity Fundamentals, and if you want to excel on the exam, you must always be aware of industry trends. Because industry trends are changing anytime and anywhere. 、
How to learn about cybersecurity, compliance, and Microsoft technology industry trends, you can do this:
- Subscribe to well-known industry news sites, blogs, and newsletters on cybersecurity, compliance, and Microsoft technologies. Examples include TechCrunch, Dark Reading, and Microsoft’s official blogs.
- Consider joining a professional association related to security and compliance, such as (ISC)², ISACA, or Microsoft’s community forums.
- Attend webinars and virtual events focused on emerging trends and technologies.
- Follow industry experts, thought leaders and official Microsoft social media accounts on platforms like Twitter and LinkedIn.
- Attend conferences like Microsoft Ignite
- Delve into research reports published by cybersecurity firms, consultancies, and industry analysts.
In short, take advantage of all the channels you can learn about cybersecurity, compliance, and Microsoft technologies to get first-hand information and prepare for high scores.
Factor 2 for Exam Victory: Practice For The Exam With The Latest Microsoft SC-900 Exam Questions
Mock practice is a great way to assess your knowledge, identify areas for improvement, and understand the format, but more importantly, to improve your ability to take the exam.
You have two ways to do the simulation:
- Microsoft’s official practice exams
- Simulation exercises provided by third parties
Officially, I won’t go into details, you can find the entry population on the Microsoft Certified: Security, Compliance, and Identity Fundamentals details page. The focus here is on third-party simulation exercises.
Choosing a third-party resource needs to meet the three elements of reliability, authenticity, and up-to-date, you can try Pass4itSure SC-900 exam questions, it all meets the requirements.
Practice The Latest SC-900 Exam Questions For Free
From:Pass4itSure Number of questions:1-15 Last updated: SC-900 Exam Questions Related: Microsoft
Question 1:
HOTSPOT
Select the answer that correctly completes the sentence.
Hot Area:
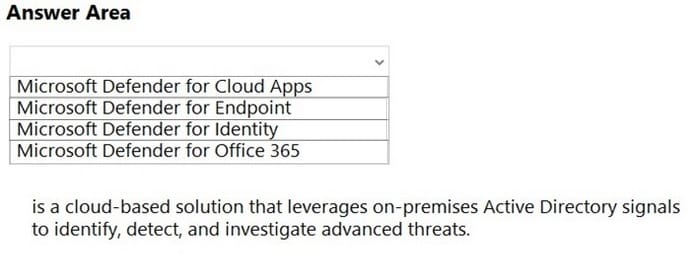
Correct Answer:
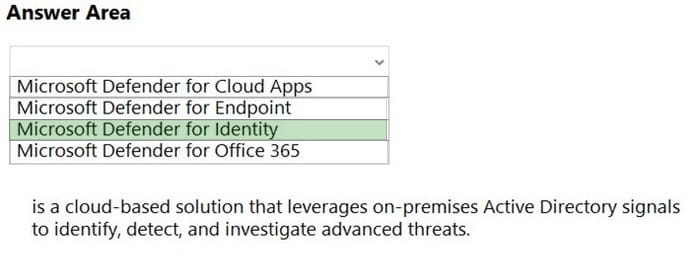
Reference: https://docs.microsoft.com/en-us/defender-for-identity/what-is
Question 2:
What is a use case for implementing information barrier policies in Microsoft 365?
A. to restrict unauthenticated access to Microsoft 365
B. to restrict Microsoft Teams chats between certain groups within an organization
C. to restrict Microsoft Exchange Online email between certain groups within an organization
D. to restrict data sharing to external email recipients
Correct Answer: B
Information barriers are supported in Microsoft Teams, SharePoint Online, and OneDrive for Business. A compliance administrator or information barriers administrator can define policies to allow or prevent communications between groups of users in Microsoft Teams. Information barrier policies can be used for situations like these:
Question 3:
A user reports that she can no longer access a Microsoft Excel file named Northwind Customer Data.xlsx. From the Cloud App Security portal, you discover the alert shown in the exhibit.
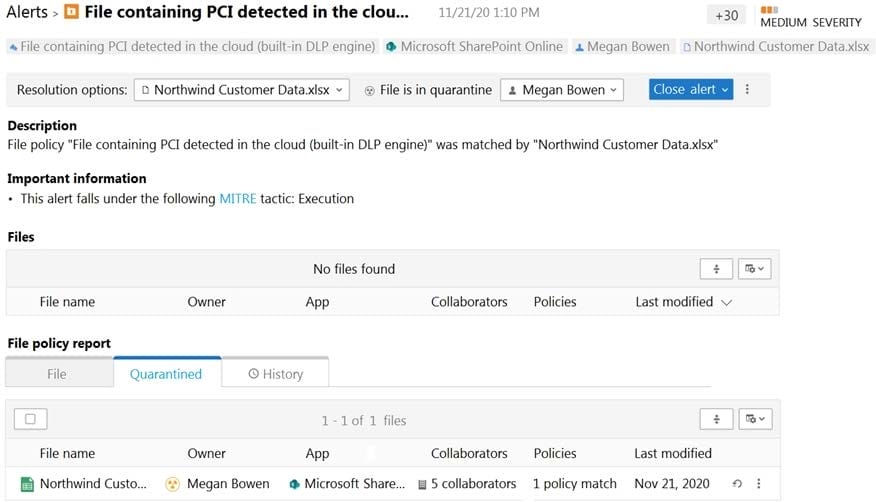
You restore the file from quarantine.
You need to prevent files that match the policy from being quarantined. Files that match the policy must generate an alert.
What should you do?
A. Modify the policy template.
B. Assign the Global reader role to the file owners.
C. Exclude file matching by using a regular expression.
D. Update the governance action.
Correct Answer: D
Question 4:
HOTSPOT
Select Yes if the statement is true for each of the following statements. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:

Box 1: Yes Box 2: Yes Box 3: No
The Zero Trust model does not assume that everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originated from an uncontrolled network.
Reference:
https://docs.microsoft.com/en-us/security/zero-trust
Question 5:
DRAG DROP
Match the pillars of Zero Trust to the appropriate requirements.
To answer, drag the appropriate pillar from the column on the left to its requirement on the right. Each pillar may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.
Select and Place:
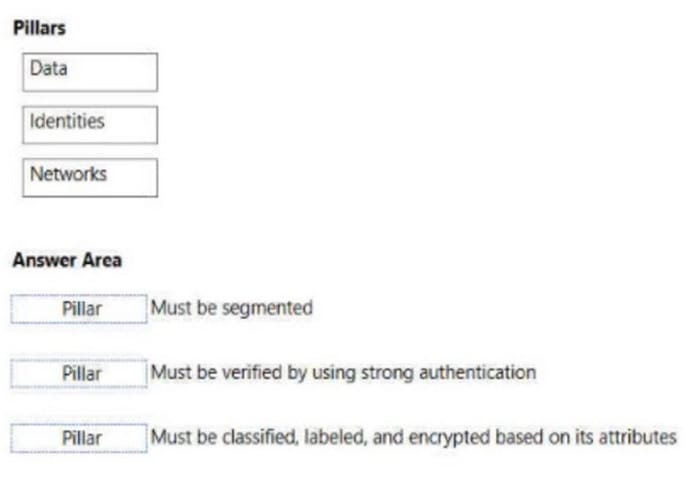
Correct Answer:
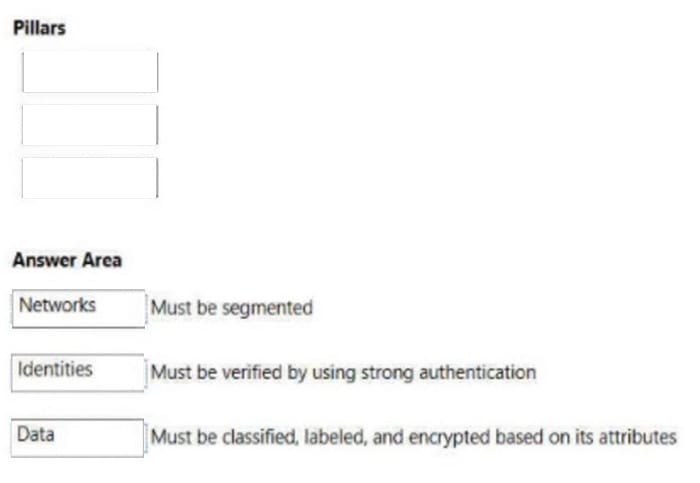
Box 1: Networks Network Ensure devices and users aren’t trusted just because they\’re on an internal network. Encrypt all internal communications, limit access by policy, and employ micro-segmentation and real-time threat detection.
Box 2: Identities Identities Verify and secure each identity with strong authentication across your entire digital estate.
Box 3: Data Data Move from perimeter-based data protection to data-driven protection. Use intelligence to classify and label data. Encrypt and restrict access based on organizational policies.
Reference: https://www.microsoft.com/en-us/security/business/zero-trust
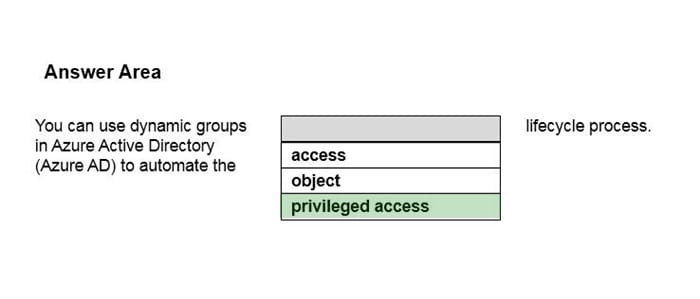
Question 6:
HOTSPOT
Select the answer that correctly completes the sentence.
Hot Area:

Correct Answer:
Question 7:
HOTSPOT
Select the answer that correctly completes the sentence.
Hot Area:
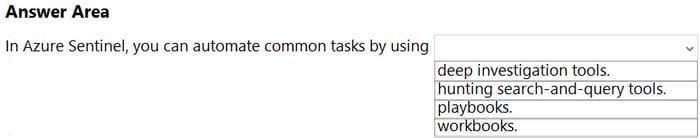
Correct Answer:
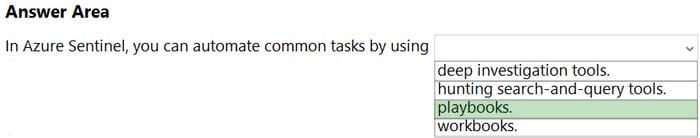
Reference: https://docs.microsoft.com/en-us/azure/sentinel/overview
Question 8:
HOTSPOT
Select the answer that correctly completes the sentence.
Hot Area:
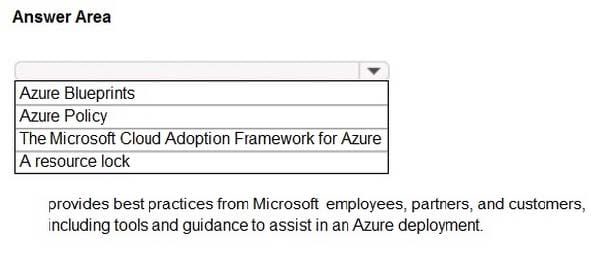
Correct Answer:
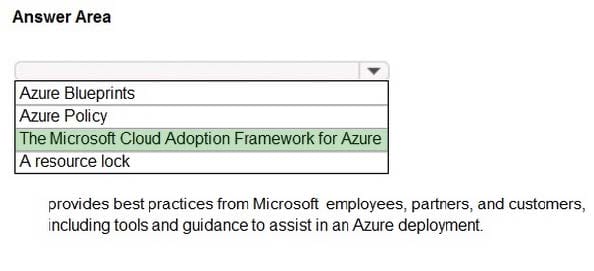
Reference: https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/get-started/
Question 9:
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
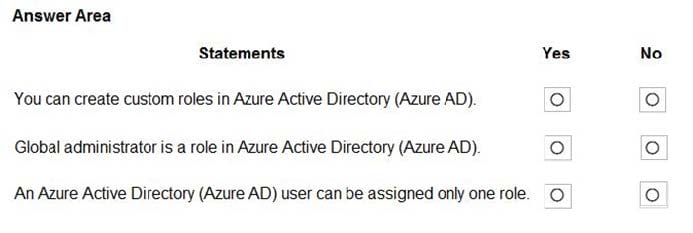
Correct Answer:
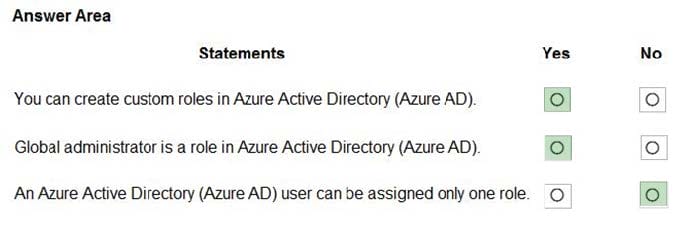
Box 1: Yes
Azure AD supports custom roles.
Box 2: Yes
Global Administrator has access to all administrative features in Azure Active Directory.
Box 3: No
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/roles/concept-understand-roles
https://docs.microsoft.com/en-us/azure/active-directory/roles/permissions-reference
Question 10:
You are implementing a data classification solution.
The research department at your company requires that documents containing programming code be labeled as Confidential. The department provides samples of the code from its document library. The solution must minimize administrative
effort.
What should you do?
A. Create a custom classifier.
B. Create a sensitive info type that uses Exact Data Match (EDM).
C. Use the source code classifier.
D. Create a sensitive info type that uses a regular expression.
Correct Answer: C
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/classifier-learn-about?view=o365-worldwide
Question 11:
Which three authentication methods does Windows Hello for Business support? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. fingerprint
B. facial recognition
C. PIN
D. email verification
E. security question
Correct Answer: ABC
Question 12:
What can you protect by using the information protection solution in the Microsoft 365 compliance center?
A. computers from zero-day exploits
B. users from phishing attempts
C. files from malware and viruses
D. sensitive data from being exposed to unauthorized users
Correct Answer: D
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/information-protection?view=o365-worldwide
Question 13:
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
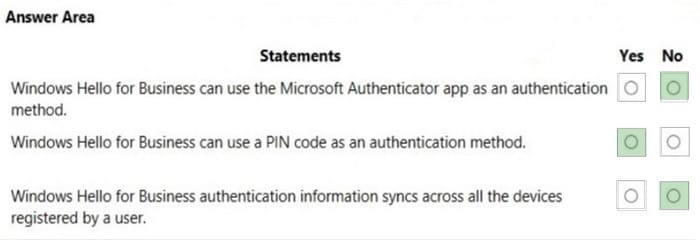
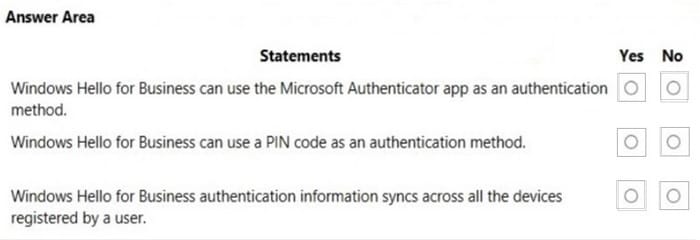
Box 1: No
The Microsoft Authenticator app helps you sign in to your accounts when you\’re using two-factor verification. Two-factor verification helps you to use your accounts more securely because passwords can be forgotten, stolen, or compromised.
Two-factor verification uses a second factor like your phone to make it harder for other people to break into your account.
Box 2: Yes
In Windows 10, Windows Hello for Business replaces passwords with strong two-factor authentication on devices. This authentication consists of a new type of user credential that is tied to a device and uses a biometric or PIN.
Box 3: No
Windows Hello credentials are based on the certificate or asymmetrical key pair. Windows Hello credentials can be bound to the device, and the token that is obtained using the credential is also bound to the device.
Question 14:
HOTSPOT
Select the answer that correctly completes the sentence.
Hot Area:
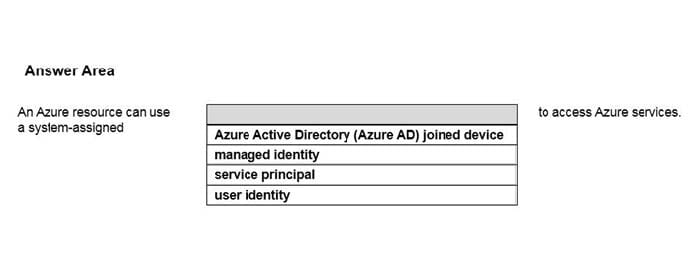
Correct Answer:
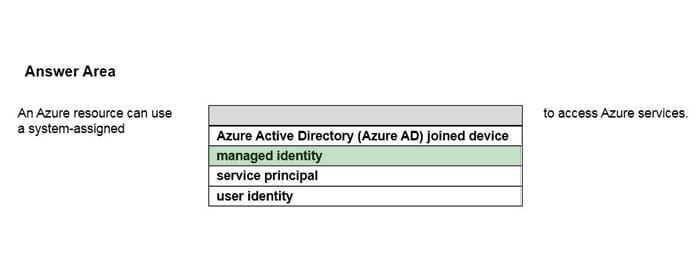
Question 15:
HOTSPOT
Select the answer that correctly completes the sentence.
Hot Area:
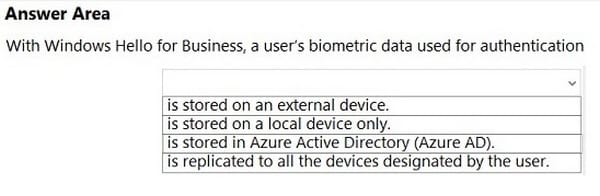
Correct Answer:
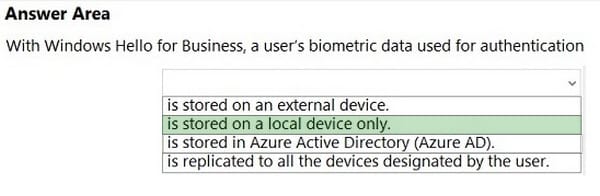
Biometrics templates are stored locally on a device.
Other Useful Resources For The SC-900 Exam
Share as a link
- Microsoft Security, Compliance, and Identity Fundamentals: Describe the capabilities of Microsoft compliance solutions – Training
- Microsoft Certified: Security, Compliance, and Identity Fundamentals – Certifications
- Microsoft Certified: Security, Compliance, and Identity Fundamentals – Certifications
- Practice Assessment
- Practice Assessment Report
- Microsoft’s new Security, Compliance, and Identity (SCI) certifications
- Microsoft 365 documentation
- Microsoft Teams admin documentation
- Welcome to Microsoft Teams
- Exam Ref SC-900 Microsoft Security, Compliance, and Identity Fundamentals
Epilogue:
While practicing the latest SC-900 exam questions and staying on top of industry trends are very effective in preparing for the SC-900 exam, there are still other things that you should not overlook and should combine them with taking online courses and training, Microsoft documentation review, and other study strategies to maximize your exam success.
How, go to Pass4itSure SC-900 Exam Questions https://www.pass4itsure.com/sc-900.html now Get the full exam questions 215+ and start your exam journey.