
Use MS-102 dumps to help you continuously improve your Microsoft 365 Certified: Enterprise Administrator Expert exam skills and stay ahead of the curve.
In this article, we will explore the benefits of using MS-102 dumps to prepare for MS-102 and provide you with free new exam practice questions shared online.
Pass4itSure Microsoft MS-102 dumps 312 Latest exam questions and answers, You can use them with confidence: https://www.pass4itsure.com/ms-102.html (pdf+vce).
New MS-102 dumps exam practice questions shared online
The information is briefly summarized below:
The 15 exam questions shared are from Pass4itSure. This is just a part of the complete Microsoft 365 Certified: Enterprise Administrator Expert MS-102 dumps, all these dumps have 312 practice questions in the MS-102 dumps.
Authentic MS-102 dumps and free new practice questions!
Question 1:
You have a Microsoft 365 E5 subscription that contains the groups shown in the following table.
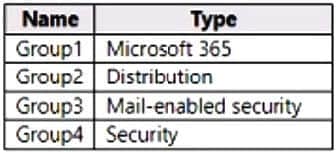
You plan to publish a sensitivity label named Label1.
To which groups can you publish Label1?
A. Group1 only
B. Group1 and Group2 only
C. Group1 and Group4 only
D. Group1, Group2, and Group3 only
E. Group1 Group2, Group3, and Group4
Correct Answer: A
In addition to using sensitivity labels to protect documents and emails, you can also use sensitivity labels to protect content in the following containers: Microsoft Teams sites, Microsoft 365 groups (formerly Office 365 groups), and SharePoint sites.
Reference:
https://learn.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels-teams- groups-sites
Question 2:
You need to configure a conditional access policy to meet the compliance requirements.
You add Exchange Online as a cloud app.
Which two additional settings should you configure in Policy1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
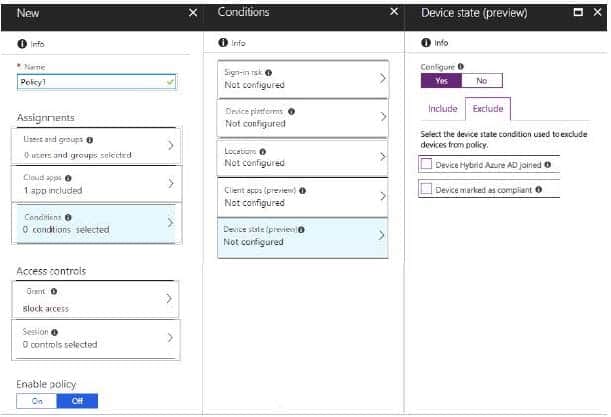
Correct Answer:
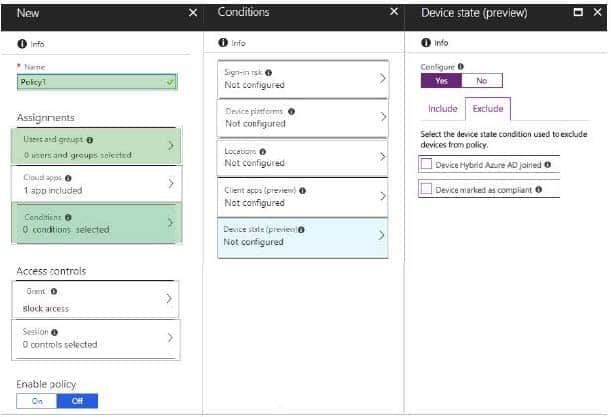
References: https://docs.microsoft.com/en-us/intune/create-conditional-access-intune
Question 3:
HOTSPOT
You have a Microsoft 365 E5 subscription that contains 200 Android devices enrolled in Microsoft Intune.
You create an Android app protection policy named Policy! that is targeted to all Microsoft apps and assigned to all users.
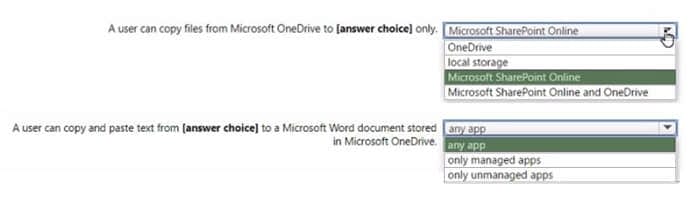
Policy! has the Data protection settings shown in the following exhibit.
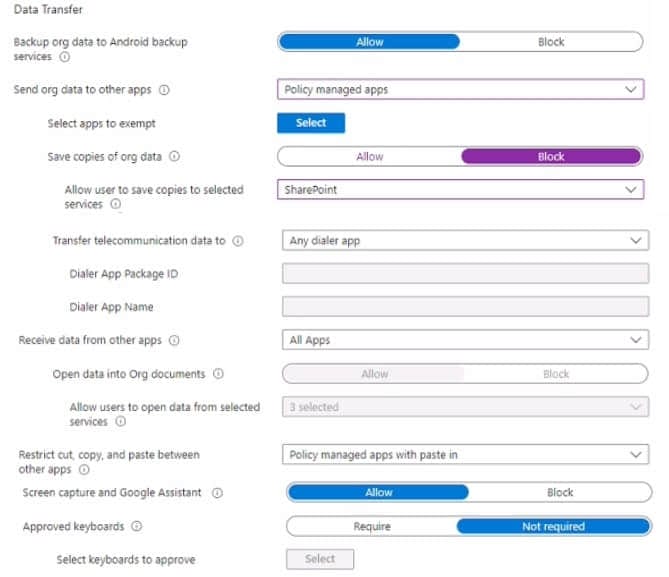
Use the drop-down menus to select \’ the answer choice that completes each statement based on the information presented in the graphic.
Hot Area:
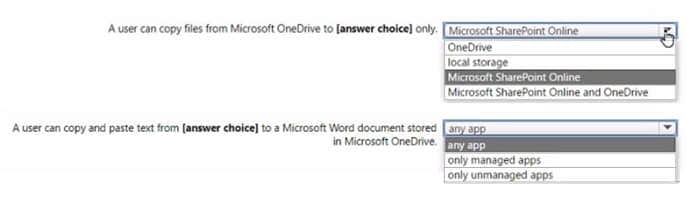
Correct Answer:
Question 4:
HOTSPOT
You have a Microsoft 365 subscription.
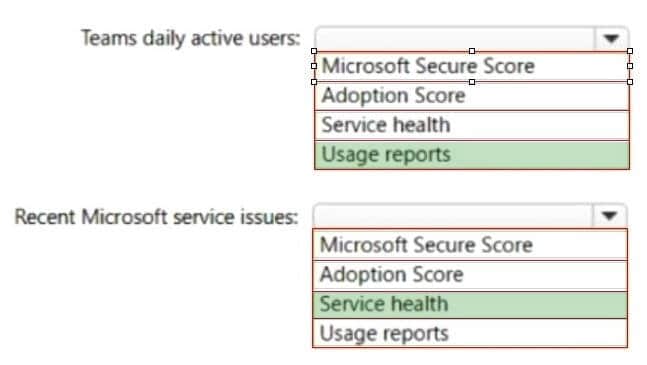
You need to review metrics for the following:
The daily active users in Microsoft Teams
Recent Microsoft service issues
What should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
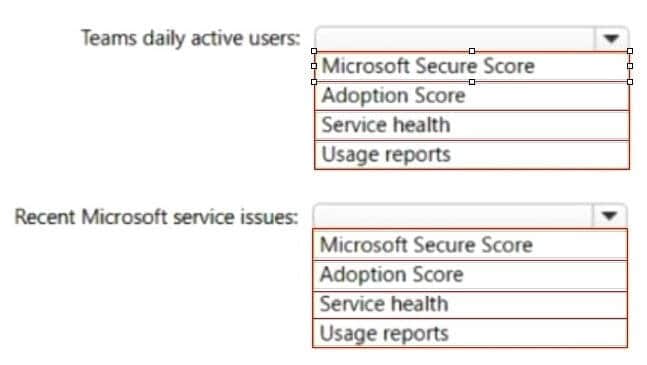
Correct Answer:
Question 5:
You have a Microsoft 365 E5 tenant.
You need to be notified when emails with attachments that contain sensitive personal data are sent to external recipients.
Which two policies can you use? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. a data loss prevention (DLP) policy
B. a sensitivity label policy
C. a Microsoft Cloud App Security file policy
D. a communication compliance policy
E. a retention label policy
Correct Answer: AD
Question 6:
You create the planned DLP policies.
You need to configure notifications to meet the technical requirements.
What should you do?
A. From the Microsoft 365 security center, configure an alert policy.
B. From the Microsoft Endpoint Manager admin center, configure a custom notification.
C. From the Microsoft 365 admin center, configure a Briefing email.
D. From the Microsoft 365 compliance center, configure the Endpoint DLP settings.
Correct Answer: D
Question 7:
DRAG DROP
Your company has a Microsoft 365 E5 tenant.
Users access resources in the tenant by using both personal and company-owned Android devices. Company policies require that the devices have a threat level of medium or lower to access Microsoft Exchange Online mailboxes.
You need to recommend a solution to identify the threat level of the devices and to control access of the devices to the resources.
What should you include in the solution for each device type? To answer, drag the appropriate components to the correct devices. Each component may be used once, more than once, or not at all. You may need to drag the split bar between
panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
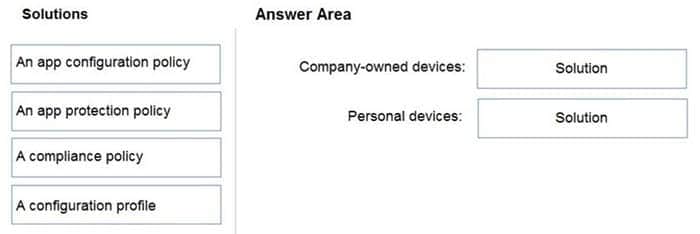
Correct Answer:
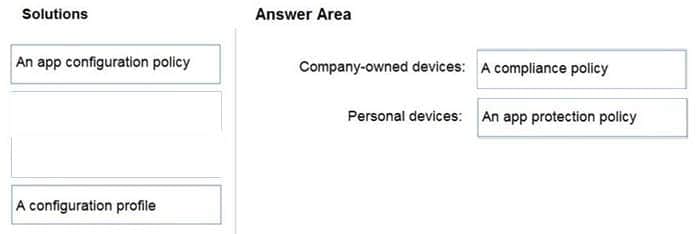
Question 8:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain named contoso.com that is synced to Microsoft Azure Active Directory (Azure AD).
You manage Windows 10 devices by using Microsoft System Center Configuration Manager (Current Branch).
You configure a pilot for co-management.
You add a new device named Device1 to the domain. You install the Configuration Manager client on Device1.
You need to ensure that you can manage Device1 by using Microsoft Intune and Configuration Manager.
Solution: Define a Configuration Manager device collection as the pilot collection. Add Device 1 to the collection.
Does this meet the goal?
A. Yes
B. No
Correct Answer: A
Device1 has the Configuration Manager client installed so you can manage Device1 by using Configuration Manager. To manage Device 1 by using Microsoft Intune, the device has to be enrolled in Microsoft Intune. In the Co-management Pilot configuration, you configure a Configuration Manager Device Collection that determines which devices are auto-enrolled in Microsoft Intune. You need to add Device1 to the Device Collection so that it auto-enrolls in Microsoft Intune. You will then be able to manage Device1 using Microsoft Intune.
Reference: https://docs.microsoft.com/enus/configmgr/comanage/how-to-enable
Question 9:
DRAG DROP
You have a Microsoft 365 E5 tenant.
You need to implement compliance solutions that meet the following requirements:
Use a file plan to manage retention labels.
Identify, monitor, and automatically protect sensitive information.
Capture employee communications for examination by designated reviewers.
Which solution should you use for each requirement? To answer, drag the appropriate solutions to the correct requirements. Each solution may be used once, more than once, or not at all. You may need to drag the split bat between panes or
scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:

Correct Answer:

Question 10:
You have a Microsoft 365 subscription.
You configure a new Azure AD enterprise application named App1. App1 requires that a user be assigned the Reports Reader role.
Which type of group should you use to assign the Reports Reader role and to access App1?
A. a Microsoft 365 group that has assigned membership
B. a Microsoft 365 group that has dynamic user membership
C. a security group that has assigned membership
D. a security group that has dynamic user membership
Correct Answer: C
To grant permissions to assignees to manage users and group access for a specific enterprise app, go to that app in Azure AD and open the Roles and Administrators list for that app. Select the new custom role and complete the user or
group assignment. The assignees can manage users and group access only for the specific app.
Note: You can add the following types of groups:
Assigned groups – Manually add users or devices into a static group.
Dynamic groups (Requires Azure AD Premium) – Automatically add users or devices to user groups or device groups based on an expression you create.
Note:
Security groups
Security groups are used for granting access to Microsoft 365 resources, such as SharePoint. They can make administration easier because you need only administer the group rather than adding users to each resource individually.
Security groups can contain users or devices. Creating a security group for devices can be used with mobile device management services, such as Intune.
Security groups can be configured for dynamic membership in Azure Active Directory, allowing group members or devices to be added or removed automatically based on user attributes such as department, location, title; or device
attributes such as operating system version.
Security groups can be added to a team.
Microsoft 365 Groups cannot be members of security groups.
Microsoft 365 Groups
Microsoft 365 Groups are used for collaboration between users, both inside and outside your company. With each Microsoft 365 Group, members get a group email and shared workspace for conversations, files, and calendar events, Stream, and a Planner.
Reference:
https://learn.microsoft.com/en-us/azure/active-directory/roles/custom-enterprise-apps https://learn.microsoft.com/en-us/microsoft-365/admin/create-groups/compare-groups? https://learn.microsoft.com/en-us/mem/intune/apps/apps-deploy
Question 11:
HOTSPOT
Your network contains an on-premises Active Directory domain.
You have a Microsoft 365 E5 subscription.
You plan to implement directory synchronization.
You need to identify potential synchronization issues for the domain. The solution must use the principle of least privilege.
What should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
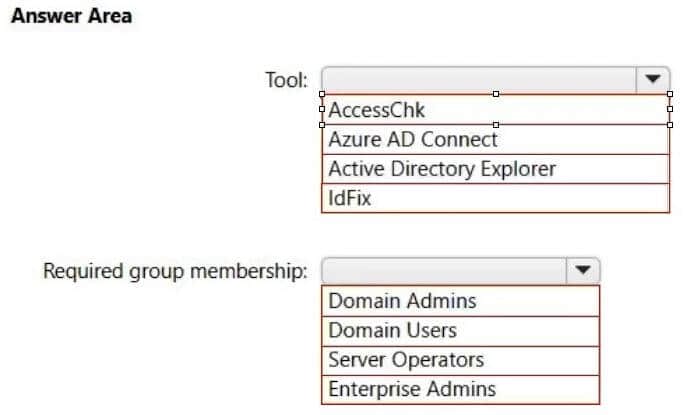
Correct Answer:
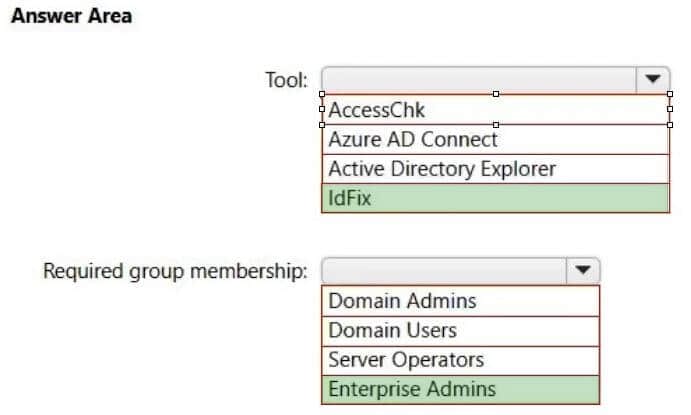
Question 12:
You have a Microsoft 365 subscription that uses Microsoft Defender for Office 365.
You need to ensure that users are prevented from opening or downloading malicious files from Microsoft Teams, OneDrive, or SharePoint Online.
What should you do?
A. Create a new anti-malware policy
B. Configure the Safe Links global settings.
C. Create a new Anti-phishing policy
D. Configure the Safe Attachments global settings.
Correct Answer: D
Safe Attachments for SharePoint, OneDrive, and Microsoft Teams In organizations with Microsoft Defender for Office 365, Safe Attachments for SharePoint, OneDrive, and Microsoft Teams provide an additional layer of protection against malware. After files are asynchronously scanned by the common virus detection engine in Microsoft 365, Safe Attachments opens files in a virtual environment to see what happens (a process known as detonation).
Safe Attachments for SharePoint, OneDrive, and Microsoft Teams also help detect and block existing files that are identified as malicious in team sites and document libraries.
Reference:
Question 13:
You have a Microsoft 365 E5 tenant.
You configure sensitivity labels.
Users report that the Sensitivity button is unavailability in Microsoft Word for the web. The sensitivity button is available in Word for Microsoft 365.
You need to ensure that the users can apply the sensitivity labels when they use Word for the web.
What should you do?
A. Copy policies from Azure Information Protection to the Microsoft 365 Compliance Center
B. Publish the sensitivity labels.
C. Create an auto-labeling policy
D. Enable sensitivity labels for files in Microsoft SharePoint Online and OneDrive.
Correct Answer: B
Question 14:
HOTSPOT
You have an Azure AD tenant named contoso.com that contains the users shown in the following table.
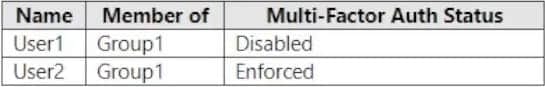
Multi-factor authentication (MFA) is configured to use 131.107.5.0/24 as trusted IPs. The tenant contains the named locations shown in the following table.
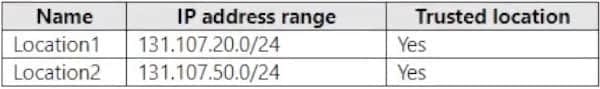
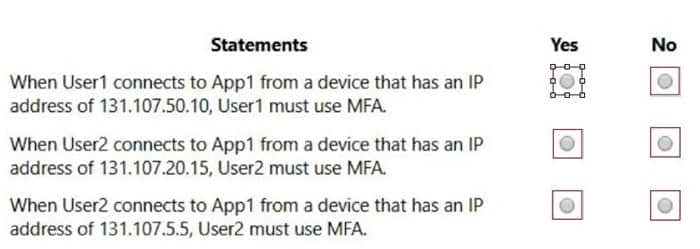
You create a conditional access policy that has the following configurations:
Users or workload identities assignments: All users Cloud apps or actions assignment: App1 Conditions: Include all trusted locations Grant access: Require multi-factor authentication For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
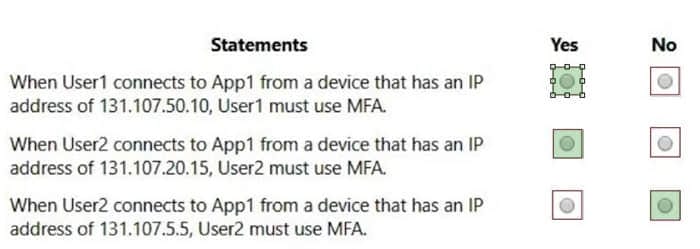
Hot Area:
Correct Answer:
Question 15:
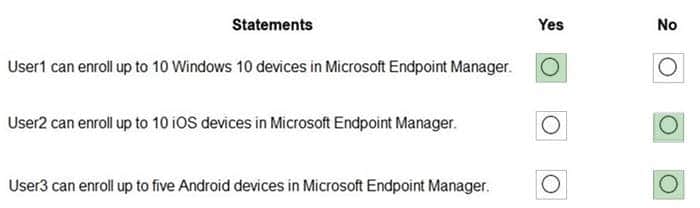
HOTSPOT
You have a Microsoft 365 subscription that contains the users in the following table.
In Microsoft Endpoint Manager, you create two device type restrictions that have the settings shown in the following table.
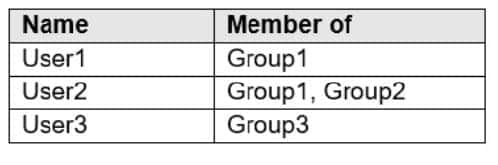
In Microsoft Endpoint Manager, you create two device type restrictions that have the settings shown in the following table.
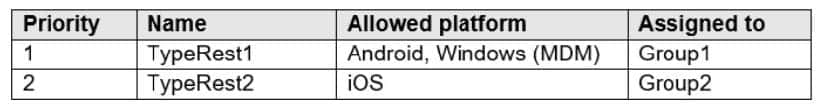
In Microsoft Endpoint Manager, you create three device limit restrictions that have the settings shown in the following table.
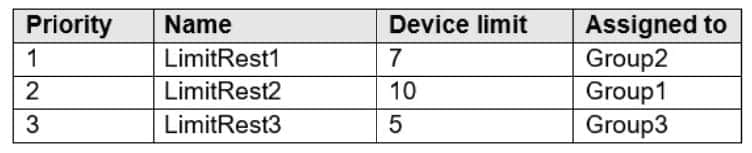
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Hot Area:
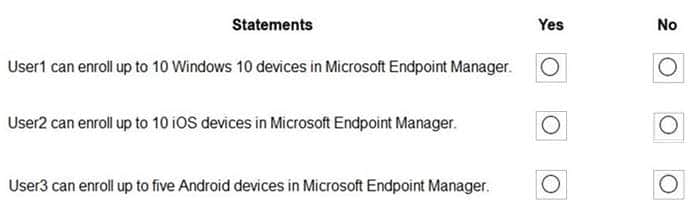
Correct Answer:
Exams related to the Microsoft 365 Administrator certification: Microsoft MD-102
More Microsoft exams here.
Learn about the benefits of using MS-102 dumps
MS-102 dumps is a valuable tool that can greatly help you prepare for the exam. They are a compilation of real exam questions and answers shared by individuals who have recently taken the MS-102 exam. By using these dumps, you can gain a wealth of knowledge and insights about the exam format, question types, and expected difficulty levels. This allows you to familiarize yourself with the exam structure and feel confident in your abilities.
One of the biggest benefits of using MS-102 dumps is the opportunity to practice Xi in real exam conditions. By trying to take a mock test using questions from the actual exam, you can simulate the exam environment and improve your time management skills. This can help you become more familiar with the test format and ensure that you are well-prepared on the day of the actual test.
In addition, MS-102 dumps provide a comprehensive overview of the topics covered in the MS-102 exam. This enables you to identify any knowledge gaps you may have and focus your Xi efforts on areas that need extra attention. By using MS-102 dumps as a Xi resource, you can simplify your preparation and improve your chances of success.
Now that we understand the benefits of using dumps, let’s dive into how to get the most out of MS-102 dumps.
How to get the most out of MS-102 dumps:
- Choose a reputable dumps provider:
Choosing a reliable and trustworthy source for your MS-102 dumps is crucial. Look for providers that have a good reputation and have received positive reviews from other individuals who have successfully used their dumps. This ensures that you have access to accurate and up-to-date information.
- Organize your study schedule:
Create a study schedule that allows you to allocate dedicated time to working with MS-102 dumps. Break your study sessions into manageable chunks and focus on a specific topic or section each time. This will help you stay organized and cover all necessary material efficiently.
- Practice regularly:
Consistent practice is the key to success when using MS-102 dumps. Set aside time each day to try the questions and answers. This will strengthen your understanding of concepts and improve your problem-solving skills.
Supplement official resources
While MS-102 dumps are a valuable learning resource, it’s also important to supplement your preparation with official Microsoft documentation and study materials. This will give you a thorough understanding of the topics and ensure you are proficient in all necessary concepts.
Study resources: https://learn.microsoft.com/en-us/credentials/certifications/resources/study-guides/ms-102
Resources for finding reliable MS-102 dumps
Given the plethora of options available online, finding a reliable MS-102 resource can be a daunting task. To help you with your search, here are some of the resources that provide reliable ones:
Official Microsoft learning: The Microsoft learning website offers a range of official Xi materials, including practice Xi tests and exam guides. These resources are designed to align with exam objectives and provide accurate and up-to-date information.
Certification forums and communities: Online forums and communities dedicated to Microsoft certification often have members sharing their experiences and recommending reliable dump providers. Engage with these communities to gather valuable insights and suggestions.
Third-Party Dumps Providers: While caution is required when accessing third-party dump providers, there are reputable sources that can provide reliable exam dumps. Look for a provider that has positive reviews and offers accurate and updated dump history. Pass4itSure is highly recommended here!
Conclusion: Unlock your success with MS-102 dumps
In conclusion, the MS-102 exam is a valuable certification that can boost your professional development and open up new opportunities. By making effective use of MS-102 dumps, you can simplify preparation, gain confidence, and maximize your chances of success. However, it is important to use the dump responsibly, supplementing it with official learning materials. With the right approach and dedication, you can succeed with the MS-102 exam and propel your career to new heights.
Ready to succeed with the MS-102 exam? Start preparing today with access to reliable and accurate MS-102 dumps (pdf+VCE) https://www.pass4itsure.com/ms-102.html from reputable providers. Combine them with official learning materials, practice regularly, and get the most out of your learning lessons. Good luck on your path to success!
